I’ve heard that song before!
 There comes a time when listening to new songs that you’ll hear a song and think, “I’ve heard that song before… or at least something very close to it.” You’re not wrong about that. There have been many songs that have either fully or partially ripped off aspects of previous hit songs. Some of these ripoff songs have landed some artists in court battles. Some ripoffs have been created at the blessing and permission of the previous artist. Some ripoffs have yet to be discovered. Let’s explore.
There comes a time when listening to new songs that you’ll hear a song and think, “I’ve heard that song before… or at least something very close to it.” You’re not wrong about that. There have been many songs that have either fully or partially ripped off aspects of previous hit songs. Some of these ripoff songs have landed some artists in court battles. Some ripoffs have been created at the blessing and permission of the previous artist. Some ripoffs have yet to be discovered. Let’s explore.
Rock, Pop, Country and even Classical works
No genre has been immune to these rip off works. Note that this author lumps all works whether by permission or not under ripoffs. Why? Because there’s no way to know WHEN the permission was obtained (i.e., before or after the fact). Some songs have only gotten permission when they’re found out. Others artists have attempted to hide the fact that their song is a ripoff of another artist.
A note to artists. When you’re caught at ripping off something from someone else, come clean and admit it. Don’t hide behind bogus arguments trying to gaslight fans and make them think yours was an original work. That’s so degrading, underhanded and disingenuous. Be honest and fess up.
Sampled Music?
This article won’t include artists who have intentionally sampled musical beats or sampled full out original recordings and then included those samples within their own works. This author classes sampled music as a direct form of plagiarism, one that is blatantly obvious to anyone who listens. Such notable sampled songs include, but are not limited to, Vanilla Ice’s Ice Ice Baby (vs Queen), Nicki Minaj’s Anaconda (vs Sir Mixalot) and The Verve’s Bittersweet Symphony (vs Rolling Stones). If you’re planning to sample someone else’s stuff, then you better get permission before you use that sample.
The songs included below are artists who either unintentionally rewrote a song they had heard in the past or intentionally ripped off portions from a past popular song, but rerecorded them again solely to improve the odds of having a radio hit. Sampling is obvious. Rerecording a backing track leaves ambiguous the interpretation of the artist’s ripoff intentions.
List of works?
Let’s get started. Below are some songs that this author is aware of, but these songs are not listed in any particular order.
Heart and Led Zeppelin
 It’s no mistake that Heart started out attempting to play and sound like Led Zeppelin (or at least a more pop-rockish version). However, Heart has ripped off Led Zeppelin on at least one occasion and landed a smash hit on the radio as a result. Unfortunately, Led Zeppelin’s original tune did not fare quite so well on the radio.
It’s no mistake that Heart started out attempting to play and sound like Led Zeppelin (or at least a more pop-rockish version). However, Heart has ripped off Led Zeppelin on at least one occasion and landed a smash hit on the radio as a result. Unfortunately, Led Zeppelin’s original tune did not fare quite so well on the radio.
Led Zeppelin song: Achilles Last Stand (1976)
Heart Song: Barracuda (1977)
Heart wholesale lifted almost all of the entire backing track from Led Zeppelin’s Achilles Last Stand (from the 1976 album Presence) including drums, bass and guitar riff and placed it directly into Heart’s Barracuda (from the album Little Queen). Heart did at least update the sound quality and sonics to sound more like Heart and less like Led Zeppelin, but the backing track is unmistakable.
Status: Unknown. Since Heart has had some of Led Zeppelin members occasionally tour with them, it is assumed that the remaining members of Led Zeppelin may have given permission to Heart. Either that or Heart may be paying royalties to the Led Zeppelin boys.
The Beatles and The Sylvers
It took a decade for this ripoff to manifest, but here it stands. While the Sylvers song Boogie Fever was a chart topping disco success in 1976, it seems to have been thanks to the Beatles. With an almost identical opening guitar riff, this song’s undertone is unmistakable. While the production sound quality was somewhat better in 1976 when the Sylvers recorded this track when compared to the 1966 track from the Beatles, the near identical lifted guitar work most definitely hearkens back to Day Tripper.
Beatles song: Day Tripper (1966)
Sylvers song: Boogie Fever (1976)
Just have a listen to this one for yourself.
Status: Unknown
The Emotions and Mariah Carey
In 1991, a budding R&B singer, Mariah Carey, burst onto the scene with her chart topping success single Emotions. The odd thing is, this ripoff was hidden in plain sight. With Mariah’s song name being identical (Emotions) to the artist name from which the song was ripped (the Emotions), how could anyone NOT see this one.
Almost the entire backing track and melody including the background chorus was lifted from The Emotion’s Best of My Love to drive Mariah’s 1991 song Emotions.
The Emotions song: Best of My Love (1977)
Mariah Carey song: Emotions (1991)
It was later publicly revealed that the track borrowed from Maurice White’s “Best of My Love“, written for the band The Emotions. This situation led to an out-of-court settlement between both sides.[4]
Status: This one didn’t go unnoticed. In fact, it eventually became known that much of The Emotions’s 1977 song Best of My Love was lifted to craft Mariah’s 1991 Emotions. This act of plagiarism resulted in a lawsuit which was settled out of court for an undisclosed sum of money… which likely means The Emotions band not only got a windfall payment from Mariah, but they likely continue to receive royalties whenever Mariah’s song plays.
The Pointer Sisters and Journey
Even big named established pop rock acts can fall prey to ripping off the works of others. In 1986, Journey was involved in a number of various band personnel issues resulting in band lineup changes, along side Steve Perry’s own personal family medical issues involving his mother’s health. Unfortunately, this band trouble left the writing and recording of a big portion of Journey’s 1986 album Raised on Radio in a quandary.
One song that came out of this difficult recording period is the Journey song entitled Suzanne, with portions of this song sounding very much lifted from The Pointer Sister’s 1982 hit, I’m So Excited.
Pointer Sisters song: I’m So Excited (1982)
Journey song: Suzanne (1986)
The drums and some of the keyboard parts are almost identical. The guitar and Steve Perry’s vocals overlaid don’t sound much like I’m So Excited, but ripping the backing track is still ripping the backing track.
Status: Unknown
The Chiffons and George Harrison
When George Harrison (and the rest) split from the Beatles to go solo, one of George’s first radio hits was 1970’s My Sweet Lord. It later become apparent that much of the sound of this song could be attributed to (or was lifted from) a 1962 hit by the Chiffons entitled He’s So Fine.
The Chiffon’s Song: He’s So Fine (1962)
George Harrison song: My Sweet Lord (1970)
Status: This comparison didn’t go unnoticed. After being noticed, George Harrison attempted to buy out the Chiffon’s catalog from its then record label owner to quash the problem. When that purchase didn’t initially work out, George was found guilty of “subconscious plagiarism” and was fined around $1.5 million. Later, the amount was reduced to around $500k after George was finally able to acquire their music catalog and renegotiate the payment.
Andy Stone (Songwriter) and Mariah Carey
Once again, Mariah Carey is alleged to have ripped off material to produce her 1994 song “All I Want For Christmas Is You”. Mariah Carey collaborated on this song with Walter Afanasieff.
Andy Stone wrote a 1989 song of the same title “All I Want For Christmas Is You”. The melody and lyrics are somewhat different, but the “vibe” of the song is mostly the same as Mariah’s, at least so Andy Stone claims. It is possible that Mariah or Walter had heard this song and decided to collab on something similar for release in 1994, or at least so Andy Stone surmises. There’s really no way to know. Both Walter and Mariah argue the recollection of this song’s origination in a way that doesn’t include having heard Andy Stone’s version. Of course Mariah is going to say that. Why would any artist choose to freely admit to ripping off someone else?
Vince Vance and The Valiants: All I Want For Christmas Is You (1989)
Mariah Carey: All I Want For Christmas Is You (1994)
Status: Lawsuit is still in progress.
Marvin Gaye Estate and Robin Thicke + Pharrell Williams
Speaking of “vibe”, here’s the song that set the vibe precedent. No longer do songs have to have notes, chords and obvious plagiarized sounds, this song (and its court result) now allow lawsuits against artists who lift the overall vibe of a song. This is a slippery slope, but let’s vibe into this one.
Marvin Gaye song: Got To Give It Up (1977)
Robin Thicke and Pharrell Williams song: Blurred Lines (2013)
Status: The estate of Marvin Gaye argued that the vibe contained within Got To Give It Up was wholly reused within Thicke’s Blurred Lines. The court agreed and awarded the estate of Marvin Gaye $7.4 million, which was reduced down to $5.3 million and then reduced again on appeal to $4.9 million plus all future royalties.
This lawsuit and its subsequent court precedent opened the door allowing “vibe” (aka. similar sounding) music cases into court. This case’s court precedent, unfortunately, has opened the door to a whole lot more music plagiarism lawsuits.
Gustav Holst and John Williams
Star Wars was both a big blockbuster experience and a phenomenon. By the time The Empire Strikes Back released into the theaters in 1980, Star Wars had fully solidified itself as a pop phenomenon. The soundtrack music for this film was no exception. In fact, it would be Star Wars that would forever change the “summer blockbuster”, striking each into the stratosphere with each and every classical beat matched to film visual cues.
John Williams not only produced some of the most recognizable themes with Star Wars, these musical themes are so closely matched to each visual film beat, such film soundtracks would become the standard by which composers must comply if they choose to score a summer film blockbuster. Before Star Wars, music was mostly an afterthought for film, something that helped carry the film, but that remained loosely tied when compared to film visual beats. After Star Wars arrived, musical and visual beats became one-in-the-same. Not only do the musical themes need to be instantly recognizable, like Star Wars and Harry Potter, but the scores need to be perfectly married and timed to each scene to maximize that scene’s visual power.
Unfortunately, there’s always a fly in the ointment. The Empire Strikes Back introduced the Imperial March which, unfortunately, seems to have been almost wholesale lifted right from Gustav Holst’s Mars, part of Holst’s The Planets suite of music. When Holst released his symphonic suite in 1918, most audience members were flummoxed. They didn’t understand what they were hearing. Thus, it received mixed to negative reviews. In fact, Holst’s Planets suite was far, far ahead of its time. Listener’s couldn’t understand it because it needed a vehicle like Star Wars visuals to carry it. That wouldn’t happen until 1977.
Once again, nabbing a theme from a past space themed composition seems an almost obvious choice for a science fiction space film. Yet, there are still many who debate this fact. Seriously, you’re going to debate the fact that the John Williams’s Imperial March sounds like Holst’s Mars? It does. There’s no way around it. There is absolutely no debate involving this track.
Gustav Holst song: Mars (1918)
John Williams song: Imperial March (1980)
Status: Holst’s Planets Suite of music is now in the public domain in the United States (and most other countries) because it was published before January 1, 1928. Still, that doesn’t make ripping material from other artists “acceptable.” Plagiarism is still plagiarism.
Spirit and Led Zeppelin
One of the most iconic and popular rock songs to emerge from the early 1970s was Stairway to Heaven by Led Zeppelin. This song inspired many guitarists. In this Led Zeppelin song, the opening acoustic guitar riff and vocal ballad slowly gave rise to a rocking powerhouse of an ending in true Led Zeppelin form.
In 1968, a band named Spirit released a track entitled Taurus. This instrumental track opens to what sounds like violins followed by an acoustic guitar riff with an uncanny sameness to the riff that opens Stairway to Heaven. Unfortunately, the song Taurus never progresses beyond that mellow acoustic, almost symphonic track. Taurus also sports no vocals. Unlike Led Zeppelin’s multipart track which begins as an acoustic ballad and slowly progresses into a heavy rocking anthem complete with vocals, drums and lyrics, Taurus as a song doesn’t take on this extended structure.
Spirit song: Taurus (1968)
Led Zeppelin song: Stairway to Heaven (1971)
Status: While the estate of the late Randy Wolfe of Spirit claimed that Stairway to Heaven was ripped from Taurus, apparently the estate found that claim difficult to prove. Led Zeppelin won the case on appeal and the court found that Stairway to Heaven did not infringe on Taurus. The estate’s appeal to the Supreme Court was denied.
However, a discerning ear can definitely tell that the acoustic riff played in Taurus to be almost identical in structure to the riff played in the opening of Led Zeppelin’s Stairway to Heaven almost note for note. Either the court has a tone deaf ear or they intentionally chose to side with Led Zeppelin for some odd reason. Additionally, it is widely known that Led Zeppelin drew near plagiaristic inspiration from many rock and blues artists from the 50s, 60s and even from those directly around them to craft many of Led Zeppelin’s hits.
To compound matters over this situation, Led Zeppelin even opened shows for Spirit on Spirit’s 1968 tour, which would have allowed Led Zeppelin to see and hear how Spirit performed Taurus. The acoustic riff between these two songs being so uncannily similar and when combined with Led Zeppelin touring with Spirit, this being a coincidence is far too improbable. With that said, the fact that Led Zeppelin took Stairway to Heaven so far beyond where Taurus went musically is likely what confused the court. Still, a riff is a riff and plagiarism is plagiarism no matter how much or for how long it was used in a song.
Alexander Cardinale + Morgan Reid and Jake Owen
As stated earlier, even Country hits are not immune to plagiarism. In 2020, Jake Owen released his song Made for You, which became a hit country song on Billboard’s country charts in 2020.
Alexander Cardinale song: Made for You (2014)
Jake Owen song: Made for You (2020)
TMZ reports that songwriters Alexander Cardinale and Morgan Reid have filed suit in Nashville, alleging that Owen’s No. 1 hit “Made for You” lifted significant portions of its structure and lyrics from their song of the same name, which dates back to 2014.
Source: Taste of Country
Once again we see that the 2014 songwriters of their earlier release Made for You claim that Jake Owen ripped off significant portions of their 2014 song to drive his 2020 release, also entitled Made for You. The duo from the 2014 song are seeking a court trial.
Status: Unknown
References
- The Biggest Music Copyright Cases in History
- Mariah Carey sued for copyright infringement over All I Want for Christmas Is You
- Wikipedia for Mariah Carey Emotions
- Songs on Trial: 12 Landmark Music Copyright Cases
- Country Star Jake Owen Sued This Legal Mess is ‘Made For You’ !!!
This article is by no means a complete list. This is just a sampling of the most visible of many of these ripped off songs. Unfortunately, now with the “vibe” precedent firmly allowed in courts, many more lawsuits will commence claiming “vibe” theft. That “vibe” ideology is that a song “feels”, but does not necessarily sound or rip off notes or ideas from a previous song. Claimants simply need to show enough proof that “vibe” was a factor.
Allowing the “vibe” idea as a defense is now a big legal risk for the music business. Any Tom, Dick or Harry can claim their insignificant little track written 5 years ago and was barely even heard, but is now being infringed by a big name star who never even heard the track. There are only so many notes on the musical scale (12 major notes to be exact, with 5 more sharp/flat notes) and only so many ways to arrange all of these. Eventually, even coincidentally, it’s far too easy to arrange those limited numbers of notes in a similar fashion without even having heard anything prior. But, there are definitely unscrupulous and greedy people willing to capitalize on and at the expense of the the hard work of others.
↩︎
Facebook Puzzle: 6÷2(1+2)
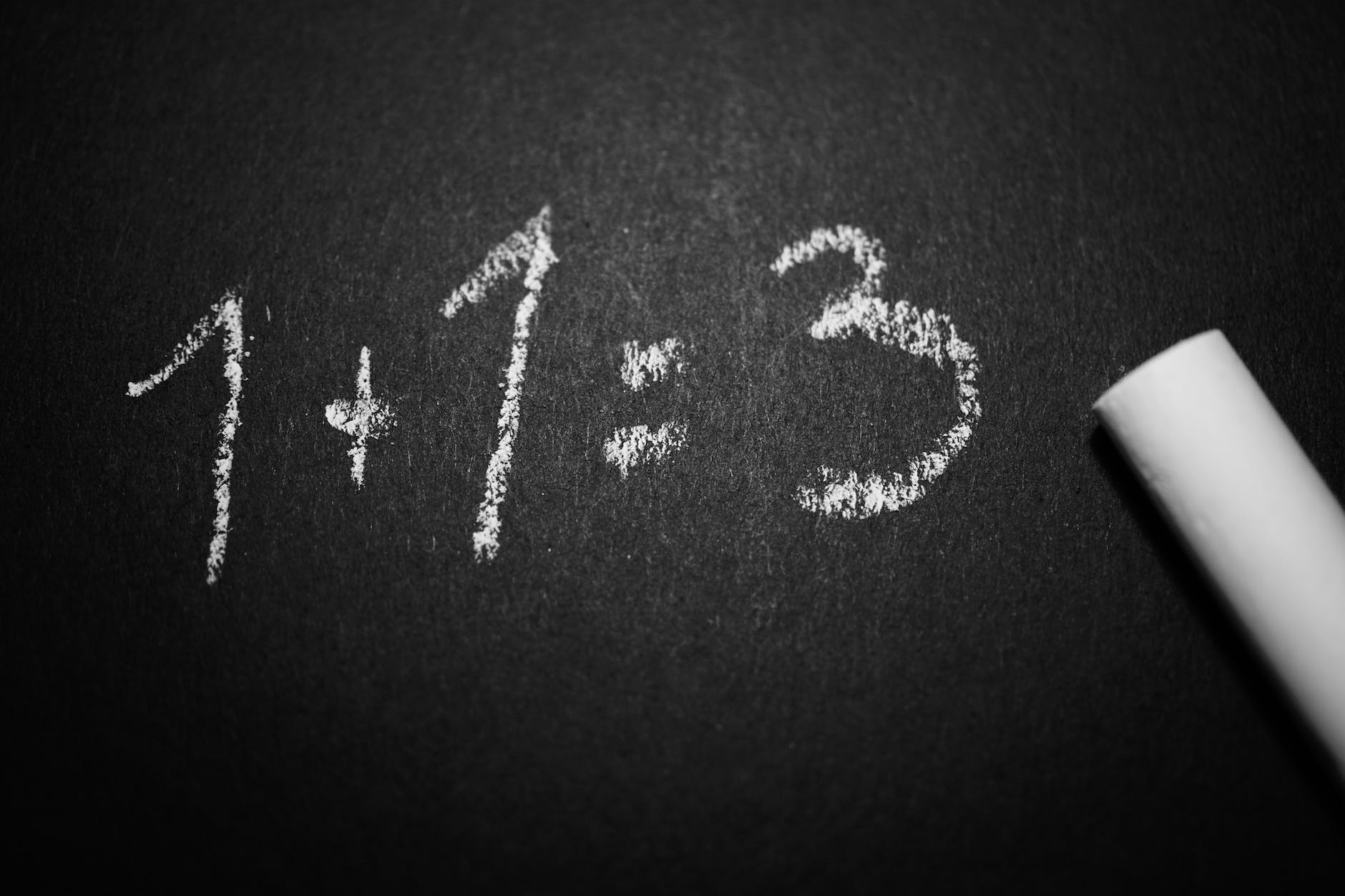
Many puzzles that pop up on many social media networks are math problems. One of these older math “problems” is 6 ÷ 2(1 + 2). Let’s explore the difficulties and controversies surrounding this math problem.
PEMDAS, BODMAS, BIDMAS & BEDMAS
These are all acronyms for more or less the same ideology. This ideology is intended to help students solve math problems logically. Unfortunately, PEMDAS and its similar ilk all have problems when it comes to certain advanced mathematical constructs… constructs that are, in fact, intentionally ignored in PEMDAS for the sake of simplicity.
PEMDAS stands for Parenthesis, Exponents, Multiplication and Division, Addition and Subtraction. BODMAS, BIDMAS and BEDMAS all utilize this same ideology, using alternative words to describe these approaches to logical math problem solving. Interestingly enough, BODMAS, BIDMAS and BEDMAS all seem to place division before multiplication, unlike PEMDAS. However, multiplication and division, at least according these problem solving helpers are supposed to be equal and performed strictly in order from left to right. In effect, the ‘DM’ order in BODMAS (and similar) or ‘MD’ order in PEMDAS make no real difference because the math problem itself dictates the order in which to solve the problem, left to right. In other words, the order takes precedence, so the ‘DM’ or ‘MD’ order listed in these helpers don’t matter.
Why PEMDAS or similar?
The PEMDAS and similar helpers were created to help grade school students solve basic math problems. This would include simple math problems like 10 ÷ (5 – 3) or (5 + 2 – 1) x 2. For those unfamiliar, the ⇝ symbol should be read as “which leads to.”
For the first problem 10 ÷ (5 – 3) that would be solved by the helpers with the following:
Parentheses first: (5 – 3) = 2 ⇝ 10 ÷ (2)
Next drop the parentheses, then solve for MD/DM: 10 ÷ 2 = 5
Answer: 5
For the second problem (5 + 2 – 1) x 2
Parentheses solved first with + and – solved inside parens l-to-r: (5 + 2 – 1) = (6)
Drop parens, multiply 6 x 2 = 12
Answer: 12
These above are simple math problems that don’t involve one key concept included in the somewhat more advanced math problem 6 ÷ 2(1 + 2). The key math concept included is …
Multiplication by Juxtaposition (aka Implied Multiplication)
Multiplication by Juxtaposition adds a level of complexity that PEMDAS and BODMAS can’t always resolve. Let’s understand why.
Multiplication by juxtaposition is a concept that gets introduced during a student’s first Algebra class. Prior to taking algebra, the concept of implied multiplication isn’t involved. PEMDAS wasn’t designed to adequately support this advanced math concept. PEMDAS, thusly, isn’t the whole truth. PEMDAS is a ruleset that works for many math problems, but not for ALL math problems. This is why PEMDAS trips up many people when attempting to use it on problems like 6 ÷ 2(1 + 2).
Before getting into this specific math problem, let’s understand a few more implied multiplication examples. An implied multiplication example is , which means 2 times a times b or
. If a = 5 and b = 2, the problem and answer would look like
. Note that * = x = times. A somewhat complex algebraic equation might be
. Solving this problem would be relatively easy as long as we know what x, y, a and b are.
The point here is not to get deep in the weeds of algebra, but instead to understand the intricacies of multiplication by juxtaposition when used in combination with PEMDAS. Juxtaposition is illustrated in problem like . Because ‘a’ and ‘b’ sit directly next to one another with nothing in between, this juxtaposition implies multiplication between these two variables. The point is, juxtaposition written in this way always implies multiplication.
Juxtaposition is a method of writing equations without the need to include the * or x symbols which explicitly state multiplication. When choosing to use juxtaposition instead of explicit symbols, this is what is called using a “style guide” for mathematical equations.
Like map legends are used to describe such information as color coding and distances on maps, style guides in mathematics describe the proper order that an equation needs to solved. Why is a style guide important? Because of the ambiguities and disparities between PEMDAS and writing equations using these shorthand methods, such as juxtaposition.
Juxtaposition is intended to help simplify the printing of equations in printed texts as well as reduce the clutter when building such complex equations. When complex equations are written, then, a style guide reference discussing precedence, levels and order of operation is imperative. Without this information printed alongside a text book, this would leave the reader in the dark, forcing the reader to utilize their own knowledge to attempt to solve the written problem.
This is exactly the problem with the Facebook problem in 6 ÷ 2(1 + 2). Because no style guide is offered, this math problem has two valid solutions; solutions that depend on which style guide you are familiar. If you subscribe to only the PEMDAS helper style guide, the answer is 9. If you subscribe to the vast majority of scientific and technical literature style guides used by STEM professionals, the answer is 1.
Let’s understand why
6 ÷ 2(1 + 2) can be written in effectively two different ways depending on which style guide you choose. The PEMDAS style guide implies the following style should be applied:
6 ÷ 2 * (1 + 2), alternatively written as .
Mathematical professional style guides would apply the following:
6 / (2 * (1 + 2)) (adding another set of parentheses for clarification)
Let’s understand these styling differences.
Under PEMDAS styling, the equation is understood as:
or more specifically,
Using scientific and engineering style guide rules, the equation is understood as:
These two equations are markedly different both in their appearance, but also in how they are solved. Under PEMDAS styling, the answer is clearly 9. Under scientific styling the answer is obviously 1.
The question is, why are there two different style guides here?
Two Style Guides?
PEMDAS (et al) is a rudimentary style guide intended to teach grade school children mathematic basics. PEMDAS is not intended to carry the child’s mathematical knowledge all the way through their life. Think of PEMDAS like a set of training wheels on your bike. The training wheels keep you upright to get the hang of balancing on your bike. Once you’ve mastered the art of balancing, the training wheels are removed.
PEMDAS is simply a set of training wheels that eventually need to be removed.
To be perfectly fair, PEMDAS should really be written as
. The PEMDAS style guide is effectively 4 components, not 6.
This updated 4 component notation means MD are at the same level and equal priority, but evaluated in order left to right. AS follows the same logic as MD, but only after MD have been resolved.
The difficulty with PEMDAS is that it was designed to be used by students NOT working with either multiplication by juxtaposition (implied multiplication — an algebra concept) or by using a slash (/) in place of the division (÷) symbol (also an algebra concept). PEMDAS expects the primary four simple operators to be explicitly used: + – ÷ x. PEMDAS breaks down when advanced operators are used because PEMDAS has no proper solution when these advanced mathematical concepts are included.
The reason for these existence of these two style guides goes back to the history of order of operations, long before even PEMDAS was coined. Most engineering and mathematics texts define that multiplication by juxtaposition is to be handled BEFORE division. In PEMDAS terms, that means the acronym becomes
where J stands for implicit multiplication by juxtaposition. When the J enters the PEJMDAS ideology, this Facebook equation is understood as:
instead of the PEMDAS understanding as
What does the division symbol ÷ mean exactly?
If you look at the ÷ symbol, it has a dot on the top and a dot on the bottom. As an abstract visual, it means “divide by”. As a literal symbol, it means move the left argument to the numerator and the right argument to the denominator. This turns 6 ÷ 2 into . Thus, the entire ÷ symbol itself is representative of defining a fraction. For ease of teaching fractions more simply, the ÷ symbol was devised to aid learners in conceptually grasping division better without involving something that visually looks like this:
in every single math problem involving division. 10 ÷ 2 is way more palatable both visually and conceptually than
. Thus, the reason the division symbol ÷ was born.
The ÷ symbol also has a sibling, the forward slash (/). This slash symbol can be used as a drop-in replacement for the ÷ symbol. When a slash is used, this then represents the two numbers as a sort of sideways or horizontal fraction, like 6/2. In STEM professional circles, both the ÷ and the x symbols are exchanged for alternatives when writing equations. Think of these changes as mature upgrades to mathematics. As we grow and learn, we adopt shortcuts which make life easier. In mathematics, juxtaposition and slash are two mature “shortcuts” in the way that equations get written. Instead of writing an equation as 6 ÷ 2(1+2), it would be written as 6/2(1+2) or if using TeX, it would appear more formally as .
Why are there TWO answers?
Good question. One that needs all of the above understanding to address. Style guides vary. The PEMDAS style guide given to early grade school students is intended to be used as a loose style guide only. Meaning, given our rudimentary understanding of mathematics at the time, PEMDAS is a helper tool that “guides” us in the right direction. PEMDAS isn’t an end-all be-all idea. It is simply a helper tool. If mathematical equations ended at the type given to us in grade school, PEMDAS is all that we would ever need.
However, moving into Algebra and higher mathematics like Trigonometry and Calculus, mathematical nomenclature must become more refined and mature… and so it does. In that goal, what PEMDAS taught us was basics. What we learn in advanced mathematics classes overrides what we learned with the basic PEMDAS logic.
Because math style guides acknowledge that there are more priority levels than the simple PEMDAS understands, our knowledge of PEMDAS must expand into that bigger understanding of more priority levels. We must take off the PEMDAS training wheels and let go of the past. We must acknowledge that there is more to mathematics than PEMDAS.
PEJMDAS is a good first step, but it doesn’t explain everything. For example, why does PEMDAS view the equation 6 ÷ 2(1+2) as instead of
?
The answer to this is really pretty simple. PEMDAS places ALL multiplication at the same level and priority as under the M. Because PEMDAS isn’t really aware of juxtaposition rules, it mistakenly moves even juxtaposed multiplication under M. PEMDAS then mistakenly turns the equation into .
The problem is that PEMDAS is taught at a time in school when juxtaposed multiplication isn’t even a concept in mathematics. As a result of juxtapositioning not being understood at that moment in a student’s mathematical learning, the student would then assume, based on PEMDAS, that ALL multiplication must roll up under that M… that’s assuming the student even understands or had been previously explained about implied multiplication. Most students learning early mathematics would likely have to ask what 6 ÷ 2(1 + 2) means. More specifically, why is a 2 sitting directly next to the (1 + 2) parentheses without an operator symbol and also what it means in this equation? This is where juxtaposition multiplication would have to be explained to the student.
In reality, in many advanced academic mathematical style guides, something that a grade school student would not be aware of, these documents state that multiplication by juxtaposition must be calculated BEFORE division. With this academic rule in place, that changes 6 ÷ 2(1 + 2) into the more widely understood and accepted .
Why is there even a question here?
Many insist that 9 is the correct answer. Yet, just as many insist that 1 is the correct answer. The disparity between these two camps comes because of one simple disagreement in math priority; a math priority that is defined by many academic and professional texts. Even many calculators have adopted this math priority rule as genuine and valid. The disparity whether multiplication by juxtaposition happens BEFORE division or whether it happens only when all general multiplication occurs in an equation is what gives rise to this equation’s dilemma.
When equations are not written in a left to right format, such as in , left to right cannot be utilized except where specifically applicable. Left to right can only be utilized IF the math problem is written using a fully left-to-right format like 6 ÷ 2(1+2). Even then, because the ÷ can be interchanged with /, a person who changes ÷ to / could then adopt the idea that 6 / 2(1 + 2) is the same as
.
Why? Because many academic style guides adopt the rule that when using a slash (/) to describe division in an equation, equations like 6 / 2(1 + 2) become the same as , thus making this equation not the same as
. In these style guides, it seems that implied parentheses are removed. For example, 6 / (2(1 + 2)) explicitly defines
. However, many mathematical style guides eliminate spurious parentheses for clarity and brevity, but they are still effectively there. In the case of this equation, adding that extra set of parentheses is actually more or less pointless because these academic style guides generally agree that EVERYTHING on the left side of the slash goes into the numerator and EVERYTHING on the right side of the slash also goes into the denominator unless there is an explicit * multiplication (or other operator) symbol present.
For example, 6 / 2 * (1 + 2) translates into , but only because the explicit * symbol is present, which prevents everything after the * from going into the denominator. When juxtaposition is in play, the previous paragraph’s rule applies.
Standards in Mathematics
What this article all boils down to is a failure to create a common ruleset of standards that everyone across all mathematical areas agree to. Thankfully, all areas of STEM professions agree by including style guide information when applicable. These style guide rules prevents confusion and misinterpretation on how to read and solve equations in a professional setting, such as in engineering, architecture and other critical areas.
What 6 ÷ 2(1+2) uncovers is the lack of generally agreed upon standards outside of professional environments. Grade school teachers and students believe that 9 is the correct answer because they’ve never been taught and have never used the style guides used by STEM professionals. On the flip side, STEM professionals don’t use PEMDAS as their leading style guide ever in their professional careers. Instead, because academia has defined specific priorities and rules regarding multiplication by juxtaposition, rules which many calculator manufacturers have adopted, this Facebook math problem only serves to uncover who was taught what.
Someone probably realized the disparity between the guide a STEM professional uses and the PEMDAS (et al) style guide(s) grade school teachers use. Then, this person decided to exploit this situation by creating this equation dilemma as a joke.
In reality, this equation only serves to show us all that consistent standards don’t exist even in mathematical circles. More than this, it shows that grade school math alone isn’t enough understand that there are two answers to this equation, with both answers being completely correct. In other words, this equation intentionally serves to disclose who follows PEMDAS and who follows more advanced mathematical style guides.
Calculator Dilemma
Some calculator manufacturers support PEMDAS, but many more support PEJMDAS as described above. As a result, unless you explicitly read the calculator user manual before you buy it, you may not understand why your calculator seems to be giving you the wrong results. In reality, it’s not giving you the wrong results. It’s giving you those results because of the disparity between the two differing style guides in use within different mathematical circles.
What does this all mean?
It means that there is no consistent teaching of the order of operations rules across all math classes across the globe. Because there are effectively two camps of people who were taught different orders of operation at differing priorities, your best bet is to write unambiguous math problems; problems that can’t have two potential answers. To do this, you’ll need to be aware of the above disparity in how order of operation is taught in mathematics in differing locations and under various instructors. Until you acknowledge that there is inconsistency in this area of mathematics, you can’t work around this problem.
The way to avoid such ambiguous problems as 6 ÷ 2(1 + 2), you can either write the problem more specifically like or you can put more parentheses into the left-to-right version of the equation so there is no difficulty for students who might have been taught a different approach. If you’re an “answer is 1” person, then write it as 6 ÷ (2 (1 + 2)). If you’re an “answer is 9” person, write it as (6 ÷ 2) * (1 + 2). Leave no question about which style to use to solve the equation.
If you are one of those stubborn folks who believes that there is and can only ever be once correct answer. Sorry to pop your bubble, but in this reality, there are technically two answers based entirely upon which style guide you adopt and/or which teacher taught you mathematics.
Are you a student?
A small disclaimer here for students. If you’re a student still in school reading this, know that there are two answers…. but also know that you need to follow your teacher’s lead. If your teacher is teaching you the “answer is 9” approach, always follow your teacher’s lead. The same goes for teachers who adopt “the answer is 1”. You want to get the best marks and that means catering to your math teacher’s approach. Know that there are two approaches that can work here, but don’t use the counter approach with your teacher unless you enjoy fighting with your teacher over your marks. As a general rule of thumb AND to make your school life a whole lot easier, always cater to your teacher’s wants, requests and whims to get the best marks and make them happy… even if you recognize those whims to be stupid.
As a student, be comfortable in your knowledge that you have recognized there are sometimes multiple ways of doing things. Know that there is absolutely nothing wrong in recognizing and booking this alternative knowledge. However, there is also no reason to fight with your instructors over knowing this information when it’s absolutely not necessary to get good marks in your class. Yes, you can be smart and know something your teacher may not. It’s also not necessary to pick a fight with your teacher over that knowledge. You never know how a teacher may respond when presented with information that’s contrary their lesson plans. You may find that many respond adversarially. It’s simpler to avoid this adversarial problem and go along with the lessons as written.
This is the trick to getting through school unscathed while also acknowledging the downsides and limitations of school curriculum. If you’re really interested in the above topic, wait until you’re in college to write and publish a paper on this very topic. Doing it this way, you can get college credit for disclosing such problems in your paper, but you can also get good grades from your teachers at the same time without being adversarial involving their teachings. Just make sure to write it for your English writing class and not as a paper for your math instructor, who might end up taking the paper far too personally or as an insult. It’s never a good idea to insult instructors, even if it’s through a well written, well researched paper.
Recap
To recap this article, the two answers for 6 ÷ 2(1 + 2) are 1 AND 9 respectively depending on which style guide you choose to adopt. Both style guides are entirely valid. Like map legends define what a map is telling you, a math style guide tells you how to solve any specific math problem.
If you are a student taking a mathematics class, only use the style guide your teacher permits. If you follow their style guide, you will always solve problems they give you with the correct answer. As for calculators, make sure the calculator you choose to buy also follows your instructor’s style guide. That means reading the calculator manual and, if possible testing the calculator. If the calculator doesn’t work as expected, return it for one that follows your teacher’s style guide.
↩︎
How to set creation file time on MacOS X

Recently, I downloaded a bunch of mp4 videos from my PS4 to create some longer form videos for YouTube with iMovie. Unfortunately, the files copied from the PS4 did not retain the original creation date and time. I was bummed because iMovie uses the creation date to sort the video clips stored in its import library.
I’m pretty sure that the PS4 stores this information with the file in the BSD operating system used on the PS4. For whatever reason, this information is lost and is not retained when copying these video files to a USB drive.
Instead, the PS4 creates the files using the current date and time of when they were copied to USB. However, the filename does includes the date and time of the PS4’s original file creation date. All is not lost. For example, one of the files is named “Grand Theft Auto V_20231021102822.mp4.” The 20231021102822 is the file’s original creation date, but it’s embedded in the filename. This is a pain in the ass, especially when you have a lot of these files and you need to depend on sorting the files by creation date.
If you’re using Linux, some of this may apply with touch, but some may not. For example, it may not be possible to set the birth time or btime in Linux. Then again, you won’t be using iMovie on Linux, so you may not encounter the same sorting problems as when using iMovie. On Linux, you’re likely to be using ShotCut. And yes, ShotCut is available for MacOS X.
Let’s explore recovering and setting the original creation date and time for these imported PS4 video files when using a Mac.
Before Getting Started / Liability Waiver / Assumption of Risk
This is a relatively deep dive tutorial and is designed for intermediate to experienced users who are comfortable running command line tools in UNIX, Linux and MacOS X. This article also expects that you are at least somewhat experienced and familiar with writing Bash shell scripts. While every care has been taken to ensure these instructions are fully accurate at the time of authorship, risk is always a possibility when running commands. Make sure you know what you’re doing and always proceed with caution when performing any shell commands.
Assumption of Risk: Should you follow any instructions provided in this tutorial, you do so at your own risk. This author and the Randocity blog holds no responsibility for how you use and/or misuse the information provided herein NOR does this author or Randocity hold any liability over any damage that may result directly or indirectly from this article’s included information. This information is provided to you AS IS. You assume all risks herein.
By proceeding with reading the remainder of this article, you agree to these terms. If you don’t agree with these terms, then navigate away NOW and go find something else to do.
Recovering Dates and Times on Files
There are two primary date/times stored as metadata with each file: creation date and last modified date. While it’s easy to set the last modification date using the ‘touch‘ command, this same command cannot be used to set the file’s creation time. Pity.
That left me looking for alternatives. If you have installed the command line development tools from Mac OS’s Xcode, there are a couple of handy command line (CLI) tools available to help with this date-setting task. These two tools are getfileinfo and setfile. Unfortunately, it seems that while the commands do get installed with Xcode, the manual pages (man pages) do not get installed. Thus, you can’t easily see or find the parameter usage of the command.
I had to refer to searching Google for the man pages for these two. Here’s the man page for getfileinfo. Here is the man page for setfile. These two commands will help get you started. If you don’t have these commands installed, you’ll need to install the Xcode command line tools.
First Step
Setting the last modification time from the above filename supplied is relatively easy by extracting the filename’s included datecode, slightly modifying it and feeding it back into the command ‘touch‘ to set the last modification date onto the file. Here’s a shell script which does just this on all files in the current directory:
#!/bin/bash
#
# setmodificationdate.sh
# FILE: "Grand Theft Auto V_20231021102822.mp4"
# DATECODE EXAMPLE: 20231021102822 => 202310211028.22
# Set IFS delimiter to EOL marker to ignore whitespace in filenames
IFS="
"
# Loop through files in current directory and update each file's last modification
# time to ${DATECODE}.${DATESS} using touch -mt [date]
for i in `ls`
do
FILE=$i
DATECODE=`echo "${FILE}" | awk '{print $4}' | awk -F "_" '{print $2}' | cut -c 1-12`
DATESS=`echo "${FILE}" | awk '{print $4}' | awk -F "_" '{print $2}' | cut -c 13-14`
# The touch command requires the date format to be YYYYMMDDHHMM.SS. Some
# conversion is required.
if [ $DATECODE ]; then
touch -mt ${DATECODE}.${DATESS} "$FILE"
echo $FILE ${DATECODE}.${DATESS} done
fi
done
The reason it’s important to update the files using the touch command first is that we’ll later use the getfileinfo command on these updated files to extract the modification date set with touch, making it easier to extract the date format which is used by the setfile command. Otherwise, if we don’t do this, we’ll have to spend a boatload of time reformatting that 20231021102822 string into the string format required by setfile. No, thanks.
Because I’m generally lazy when I see other easier formatting alternatives, I don’t wish to spend a full day of shell scripting on reformatting strings when I don’t have to. Since both the last modification and creation dates should be set identically, using two different commands is the easiest way to get these files back to their original dates.
Second Step
After having updated the last modification date of each of the video files using ‘touch‘, we’re halfway there. The other half is updating the creation date using the ‘setfile‘ command. Right now, even though the modification date is updated, the creation date is still set to the date and time when the file was copied from the PS4 onto the USB drive. I’m still at a loss why PS4’s Capture app does this. No reason to dwell on stupidity from Sony. Let’s move on.
If you would like to see the current creation date on the files, check it with following command:
$ ls -lhU -rwxrwxrwx 1 owner staff 334M Oct 21 20:10 Grand Theft Auto V_20220826114603_1.mp4 -rwxrwxrwx 1 owner staff 452M Oct 21 20:05 Grand Theft Auto V_20220918194930_1.mp4 -rwxrwxrwx 1 owner staff 390M Oct 21 20:04 Grand Theft Auto V_20220922235359_1.mp4 -rwxrwxrwx 1 owner staff 398M Oct 21 20:04 Grand Theft Auto V_20221002025349_1.mp4 -rwxrwxrwx 1 owner staff 347M Oct 21 20:03 Grand Theft Auto V_20221007034124_1.mp4 -rwxrwxrwx 1 owner staff 389M Oct 21 20:03 Grand Theft Auto V_20221013095807_1.mp4 -rwxrwxrwx 1 owner staff 1.3G Oct 21 20:00 Grand Theft Auto V_20221022131151_1.mp4 -rwxrwxrwx 1 owner staff 342M Oct 21 20:00 Grand Theft Auto V_20221113174109_1.mp4 -rwxrwxrwx 1 owner staff 55M Oct 21 20:00 Grand Theft Auto V_20221124014001_1.mp4 -rwxrwxrwx 1 owner staff 389M Oct 21 19:59 Grand Theft Auto V_20221211111225_1.mp4 -rwxrwxrwx 1 owner staff 288M Oct 21 19:59 Grand Theft Auto V_20221213064150_1.mp4 -rwxrwxrwx 1 owner staff 419M Oct 21 19:58 Grand Theft Auto V_20221223001116_1.mp4 -rwxrwxrwx 1 owner staff 414M Oct 21 19:58 Grand Theft Auto V_20221230055654_1.mp4 -rwxrwxrwx 1 owner staff 77M Oct 21 19:57 Grand Theft Auto V_20230108204052_1.mp4 -rwxrwxrwx 1 owner staff 427M Oct 21 19:57 Grand Theft Auto V_20230108210502_1.mp4 -rwxrwxrwx 1 owner staff 133M Oct 21 19:57 Grand Theft Auto V_20230114165648_1.mp4 -rwxrwxrwx 1 owner staff 471M Oct 21 19:56 Grand Theft Auto V_20230205042420_1.mp4 -rwxrwxrwx 1 owner staff 441M Oct 21 19:55 Grand Theft Auto V_20230222025805_1.mp4 -rwxrwxrwx 1 owner staff 424M Oct 21 19:54 Grand Theft Auto V_20230227022823_1.mp4 -rwxrwxrwx 1 owner staff 373M Oct 21 19:54 Grand Theft Auto V_20230307124853_1.mp4 -rwxrwxrwx 1 owner staff 420M Oct 21 19:53 Grand Theft Auto V_20230311090033_1.mp4
To see the last modification time set from above touch command, use the following:
$ ls -lh -rwxrwxrwx 1 owner staff 334M Aug 26 2022 Grand Theft Auto V_20220826114603_1.mp4 -rwxrwxrwx 1 owner staff 452M Sep 18 2022 Grand Theft Auto V_20220918194930_1.mp4 -rwxrwxrwx 1 owner staff 390M Sep 22 2022 Grand Theft Auto V_20220922235359_1.mp4 -rwxrwxrwx 1 owner staff 398M Oct 2 2022 Grand Theft Auto V_20221002025349_1.mp4 -rwxrwxrwx 1 owner staff 347M Oct 7 2022 Grand Theft Auto V_20221007034124_1.mp4 -rwxrwxrwx 1 owner staff 389M Oct 13 2022 Grand Theft Auto V_20221013095807_1.mp4 -rwxrwxrwx 1 owner staff 1.3G Oct 22 2022 Grand Theft Auto V_20221022131151_1.mp4 -rwxrwxrwx 1 owner staff 342M Nov 13 2022 Grand Theft Auto V_20221113174109_1.mp4 -rwxrwxrwx 1 owner staff 55M Nov 24 2022 Grand Theft Auto V_20221124014001_1.mp4 -rwxrwxrwx 1 owner staff 389M Dec 11 2022 Grand Theft Auto V_20221211111225_1.mp4 -rwxrwxrwx 1 owner staff 288M Dec 13 2022 Grand Theft Auto V_20221213064150_1.mp4 -rwxrwxrwx 1 owner staff 419M Dec 23 2022 Grand Theft Auto V_20221223001116_1.mp4 -rwxrwxrwx 1 owner staff 414M Dec 30 2022 Grand Theft Auto V_20221230055654_1.mp4 -rwxrwxrwx 1 owner staff 77M Jan 8 2023 Grand Theft Auto V_20230108204052_1.mp4 -rwxrwxrwx 1 owner staff 427M Jan 8 2023 Grand Theft Auto V_20230108210502_1.mp4 -rwxrwxrwx 1 owner staff 133M Jan 14 2023 Grand Theft Auto V_20230114165648_1.mp4 -rwxrwxrwx 1 owner staff 471M Feb 5 2023 Grand Theft Auto V_20230205042420_1.mp4 -rwxrwxrwx 1 owner staff 441M Feb 22 2023 Grand Theft Auto V_20230222025805_1.mp4 -rwxrwxrwx 1 owner staff 424M Feb 27 2023 Grand Theft Auto V_20230227022823_1.mp4 -rwxrwxrwx 1 owner staff 373M Mar 7 2023 Grand Theft Auto V_20230307124853_1.mp4 -rwxrwxrwx 1 owner staff 420M Mar 11 2023 Grand Theft Auto V_20230311090033_1.mp4
Note that once a file’s date is considered “too old”, the ls command no longer shows the time of the file, only the “MM DD YYYY” date. The time is still there on the file, but it’s simply not shown. With ls, this will have to do.
Extracting the Date for Setfile
To extract the date string format needed for setfile, we’ll use the getfileinfo command on the now touched files. That’s done with the following:
$ getfileinfo -m "Grand Theft Auto V_20231021102822.mp4" 10/21/2023 10:28:22
The getfileinfo -m command returns the last modified date string in the date string format “10/21/2023 10:28:22”, which is a properly formatted string to immediately use with setfile -d. Thankfully, we just set this date on the file above. This output string value from getfileinfo should match the date value in the filename. If the date value doesn’t match, the touch command above might not have worked correctly.
To set the creation date on the file, we will use the following:
$ setfile -d "10/21/2023 10:28:22" "Grand Theft Auto V_20231021102822.mp4"
The -d option is used to set the creation date on the file. This command only changes one file, though. Not very helpful since we’re needing to update a bunch of files all at once. To do this, we’ll need a shell script for batch changes.
#!/bin/bash
#
# setcreationdate.sh
# Set field separator to EOL marker to ignore whitespace in filenames
IFS="
"
# Loop through files in current directory
for i in `ls`
do
FILE=$i
# Extract properly formatted creation date using getfileinfo
FCREATEDATE=`getfileinfo -m ${FILE}`
# Update creation date using setfile with date extracted from getfileinfo
# above, stored in FCREATEDATE
setfile -d "${FCREATEDATE}" "${FILE}"
echo ${FILE} done
done
Both of these shell scripts have been tested and worked perfectly to update the creation and modification dates on all of my PS4 video files back to their original dates recorded.
How do I use the scripts?
To use the above scripts, simply copy and paste them into your favorite MacOS X editor such as ‘vi’ or TextEdit, then save each script to whatever name you like. I named them setmodificationdate.sh and setcreationdate.sh, respectively. You can name them however you like. To make the script executable, do this with the following command:
$ chmod 755 scriptname.sh
Do these scripts work with vFAT formatted drives?
Yes, they do. These tools will work with vFAT as well as HFS+.
Is this the only way to change file dates?
No, there are other ways. You can use tools like ‘uuencode’, ‘tar’, ‘cpio’ or maybe even ‘zip’ to create an archive backup, then modify the dates inside the backup, then restore the files with newly updated dates. This is more complicated. The above is a simpler solution than mucking about with backup and restore processes. However, this archive solution may be the only way forward on operating systems that don’t allow modification of the creation dates on live files.
Why do all of this?
The iMovie app has an import library. In this imported clip library, the sorting feature uses the creation date, not modification date to sort the files. To make sure iMovie can sort these files properly date ascending, the creation date must be set correctly. Because copying the files to USB from the PS4 reassigns the date the mp4 was copied to the USB, not the date it was originally created on the PS4, this makes sorting from oldest to newest in iMovie a big problem.
When attempting to create a new movie using PS4 clips in chronological order, not having correct datestamps on each file makes it a challenge to locate the correct clips in the iMovie library. To correct for this, setting the creation date stamps on all of the mp4 files allows iMovie to sort them in the correct order, rather than sorting them based on the random date they were copied to the USB drive.
Note that once you have updated the dates on the mp4 files, you’ll need to restart iMovie to make sure it sees the newly updated dates on the files. iMovie won’t see these file changes until it’s been restarted.
Good luck and happy rendering!
↩︎
Rant Time: News Networks are Failing Us!

This rant is a long, long time coming. News network media has been in serious decay for going on at least a decade. Recently, however, news networks are now a danger to the United States and, specifically, to the world… just as the GOP is decaying democracy itself. The whole country is in a state of decay… entropy, if you will. News media is not an exception to this state of decay. In fact, news media is ONE cause of it.
Let’s rant!
Cable News Networks
The vast majority of news is now obtained by viewers using one of the 3 main cable news networks, CNN, MSNBC and Fox News, with broadcast news sources like ABC News and CBS News leaning into this same exact problem. Even audio podcast sources like NPR, Reuters and the Associated Press are also throwing their hat into this same overkill ring.
You might be asking, “But aren’t there now 4 cable news networks?” Yes, the newest addition to cable news, [NEWSNATION] (formerly WGN), is also making a play for a slice of the cable news audience. However, [NEWSNATION] is still still too new to be considered fully. Yet this up-and-coming new channel is making all of the same mistakes as the incumbent news channels. Nothing news to see here, move along.
[NEWSNATION]
Let’s discuss this newest addition to cable news, [NEWSNATION]. This news company, which was born out of WGN in the long past, is now trying to resurrect an older WGN national news idea into NewsNation (note, the caps, formatting and brackets will be dropped for the remainder of this article).
NewsNation claims to offer a more fair and balanced approach to news reporting. Yet, NewsNation is falling into the same exact unbalanced and nonsensical news traps as every other cable news network. One only needs to watch NewsNation to understand its imbalance and unfairness in its reporting. If NewsNation cannot get itself on the right track when the rest of the news networks are doing these same exact wrong things, then 24 hour news networks cannot and will not survive.
I had hopes that NewsNation would take a different tack from CNN, MSNBC and Fox News. Unfortunately, NewsNation management has decided to adopt all of the same wrong postures and same failing strategies that the rest of the so-called news channels have adopted. Come on guys, try something different!
National Politics vs War
All of these news networks get so deep in the weeds with tunnel vision, that they cannot understand how unbalanced and unfair their news reporting actually is. These channels all seem to think their reporting is fair and balanced. How balanced can news reporting be when EVERY SINGLE NEWS CHANNEL focuses solely on one story 24 by 7 to the exclusion of all else?
It would be one thing if only one of these news channels chose to delve deep into a topic. When every single one of these channels simultaneously choose to dive deep and focus their entire 24 hour news cycle to a single topic, that’s called myopia or tunnel vision.
What’s worse is that this Israeli conflict is a regional conflict that has existed for decades. There is absolutely nothing new about this conflict. This conflict had been in hiatus most recently, but that doesn’t make this conflict new. It is different in how it began this time, yes, but it’s the same old religious arguments rehashed all over again. And yet, CNN, MSNBC and the rest are reporting this conflict as though it’s never existed before (said in total surprise). There’s nothing surprising or new about any of this conflict.
This specific Israeli clash also isn’t the problem behind this national news reporting crisis. It’s simply a victim of and catalyst for just how crappy, inane, unintelligent and one-tracked our national news cycles have become.
Gaza Strip Reporting
As of this article, Israel is now at war with Hamas over, once again, the Gaza Strip. The Gaza Strip is a contentious bit of “holy” land that both the Palestinians and the Jewish claim for their respective religions. This small bit of land, which is approximately twice the size of Washington D.C., has always been claimed by both religious sects as “holy land” under their religious doctrines. As a result of these two separate religions claiming this same small piece of land, tensions erupt, tempers flare and eventually missiles get launched. Any person who chooses to live on this contentious bit of land must choose to live with the consequences of that decision. You could choose to live anywhere else safer, but CHOOSING to live on the Gaza strip comes with it the very real possibility of death and destruction for you, your family and your loved ones. This most recent Israeli and Hamas clash proves this point out.
Each side believes the other shouldn’t be entitled to live on or inhabit this piece of land. That the land exists to serve only one of the two religions. Because both sides tend to wholly believe in this claptrap, this war will never truly end… a war over a silly little piece of real estate that, may or may not at some point in the past been used by any specific religion. Any holy nature of that land is long, long past. Yet, both the Palestinians and the Israelis feel the need to continually lob missiles at one another, killing and wounding many… all over this smallish piece of real estate.
Why is this historical backdrop important? Because the war over the Gaza strip has never, ever ended. It may have gone into a brief (in historical terms) remission, but it has never firmly ended. More than this, it can never truly end so long as both factions remain.
Tunnel Vision Reporting
News networks are treating this Israeli vs Hamas war as though it’s brand new, like it’s never ever existed before. Anyone with half a brain knows the insincerity of this reporting. Additionally, someone (stupid) at each one of these news networks mistakenly believes that the Gaza strip conflict is something that America needs to know about and watch 24 by 7 around the clock for days on end. Hint: we don’t need or want this.
Instead, what we as viewers are being treated to (no, being tortured with) is a tunnel vision news reporting. Worse, every single news outlet is doing this same exact thing. Instead of reporting (f)actual news around the United States, news which is way more important to United States viewers; instead we’re getting play-by-play, missile-by-missile, Israeli-by-Palestinian reporting with boots on the ground in Israel. This is reporting that doesn’t directly impact most Americans, except for Israeli-American or Palestinian-American compatriots or for those few military enthusiasts. If you’re that much of a military aficionado, go hop a plane and head over to the Gaza strip. Enjoy your up close and personal view. No one is stopping you. For that matter, if you’re that much of a military enthusiast, go hop another plane and head to the Ukraine front lines.
The entirety of the Jewish population is a demographic that accounts for just 4.5% of the entire United States Population. Israeli-American immigrants might account for as few as 140,000 in total (0.0424% of the entire US population). The Palestinian population numbers around 170,000 (0.05152% of the entire US population). Who knows how many are military enthusiasts there are… but news networks shouldn’t ever cater their news reporting to this small group of macabre viewers.
Why are these numbers important? They’re important to identify the total possible number of people who might be interested in watching news on this topic AND who live IN the United States. MSNBC, CNN and Fox News are primarily news networks targeting United States viewers, a total population of around 330 million, with a much smaller number watching. CNN additionally offers a broader and separate CNN International news channel designed specifically to showcase international news across the globe. CNN, if you want to broadcast international 24 by 7 coverage, use your CNN International channel instead.
However, every last one of these news networks has decided to devote 100% of their 24 by 7 coverage to this age old Israeli + Palestinian conflict, choosing to ignore all other important news reporting (save the occasional political snippet). It doesn’t matter what time of the day or night you tune in, you can be guaranteed that within 5 minutes or less, the news host will speak or the chyron will display the word “Hamas”, “Israel” or “Gaza”.
THIS is tunnel vision news reporting. There is also nothing fair or balanced about operating tunnel vision reporting, especially when EVERY SINGLE NEWS CHANNEL is doing this. When you can tune into a news network and hear about Hamas at 8am, 12pm, 7pm, 11pm or 5am, news reporting is in tunnel vision mode; a mode that is to the detriment of the United States and its viewers. It might even be considered a national safety problem.
Demographics and Viewership
When the biggest audience you can expect over this conflict is perhaps 5% of your total viewers, including both Palestinian-American immigrants, Israeli-American immigrants and the broader Jewish population (a sub-population who might or might not hold interest in that area’s conflict), you’re barking up the wrong tree by devoting 24 by 7 tunnel vision reporting to Israel. Even then, America has ~330 million total population, but only a small portion of those viewers are actually watching 24 by 7 cable news.
Fox News claims to have the biggest audience share at 1.57 million simultaneous viewers. Unfortunately, we also know that Fox News lies like a cheap rug. Any viewership numbers that Fox News claims are likely falsified, either because the Murdochs have paid off the statistic gathering company or they own that company allowing them to fabricate any numbers they wish. The point is, Fox News very likely has way fewer than its purported 1.57 million viewers claimed. Fox News has proven itself to be untrustworthy. Yes, that would also include fabricating its viewership numbers.
The point here is that even if 1.57 million viewers is anywhere close to real (and we know that it isn’t), 5% of that is 78,000 simultaneous viewers.
This means that any news network that chooses to devote 24 by 7 news coverage to Israel, does so to appeal to, at most, 78,000 Americans. Even then, that number is likely drastically lower… perhaps even as low as 10,000 – 20,000 people. Seriously, 24 hour coverage solely to interest around 20k viewers? Are news producers really this insane? I guess so.
And yet, these news networks wonder why we are seeing…
News Reporter Hostages and Deaths?
Hello! You’ve devoted your entire 24 hours of news cycle coverage into an age old, no-holds-barred, Geneva-convention-breaking set of warring factions… all for the benefit of less than 50,000 viewers? These factions have been warring for as long as everyone today on this planet has been alive… longer even. This is a Jihad, a holy war, a religious conflict. Do you think that either of these two sides legitimately believe in such things as the Geneva convention? While many of these spokespersons state that they uphold this convention, what they say and what they do are two drastically different things.
It’s easy to state that a given nation state upholds the Geneva convention, it’s an entirely separate thing to actually do it. You need to look at their actions, not at their words. Words are easily empty platitudes, especially from that area of the world. When ages old religious wars recur, specifically in that specific area of the world, the war, devastation and death toll to the other side is what’s important, not upholding some arbitrary convention that neither side agreed to when the war originally began.
When reporter hostages are taken and when some of these reporters are summarily executed, you can’t then wonder why it happens. You can blame them. You can point fingers at them. You can even yell at them. However, the fault here is on the news network management team for insinuating THEIR staff into a dangerous age old conflict. Your news network chose to insert people into a very dangerous situation and then you wonder why some reporters die? Get with the program.
Should News Networks Report on the Israel conflict?
Yes, but do so with an appropriate amount of designated time based sanely on the demographics who might show interest in watching. 24 by 7 coverage of ANY event needs to be considered carefully. Yet, it’s entirely clear that no producer or management team member at these organizations is questioning this decision.
Let’s understand why it’s important to temper coverage. First and foremost, this is NOT an American conflict. The United States has no stake in the Israeli “war”. While America is an ally to Israel, that ally status doesn’t include the United States immediately jumping into this age old conflict nor should we become directly involved in that nation state’s religious conflicts.
America has no interest or stake in Israel other than our ally status. While the American military can help Israel in small ways, it is up to Israel to fully manage its own conflicts, in the same way as Ukraine must manage its own conflict with Russia. We can give aid and support (whatever hands-off form that takes) to Israel as an ally, that doesn’t and shouldn’t include American military boots-on-the-ground or planes-in-the-air support against Hamas. That conflict is all on Israel.
News Networks and Ukraine
News networks have long given up 24 by 7 coverage of the Ukraine war. It started out with 24 by 7 play by play coverage, but soon (within a month or so) gave way to United States news coverage. The Ukraine war coverage is now placed where it should be… with maybe 5-10 minutes of coverage every one to two hours.
This is the amount of coverage Israel should be given right now. In other words, the news networks are giving too much coverage to the Israeli conflict. It’s not like this conflict started just recently. This conflict has been in progress for years and years and years. Sure, it’s once again erupted recently, but it’s a conflict that’s been ongoing for many years.
TOO MUCH COVERAGE!
Here we have finally arrived at the entire point of this article. News channels are now beating a dead horse with the unnecessary and improper choice of sweeping 24 by 7 coverage over situations that honestly warrant at most 10 minutes of coverage once an hour… and they’ve been playing this over-reporting game for several years. Not only are they beating this specific story to death, they’re bludgeoning every single story like this into dust. News coverage must be tempered. Tempered with good taste. Tempered against the demographics watching. Tempered against the interest by viewers (i.e., ratings). It must be given the seriousness of coverage that all news is given. BUT… news coverage must not preempt all other news for days on end, especially when that coverage is over a situation that is not in the United States AND a situation that is an ongoing conflict that has roots in years long past.
While all of us in America grieve for those affected in this unfortunate Israeli-Hamas situation, there’s a substantial difference between grieving and spending so much time in a news cycle that news networks beat their news coverage to death.
News producers need to take a long hard look, not only at themselves, but at their news networks. By having tunnel vision reporting over events like this one; events which ARE serious, but are also not alone worthy of 24 by 7 news coverage, news networks are now failing America hard.
By preempting news stories of equal import within the United States solely to cover a situation outside of the United States with excessive coverage, Americans are being left in the dark as to what’s happening in their own states. That’s not news reporting. That’s neglect. That’s wilful abandonment of each news network’s responsibilities to cover ALL news equally and fairly.
There can be no equal and fair when news networks willfully abandon coverage of domestic news in favor of Israel… a country that has almost nothing to do with America.
NewsNation, MNSBC, CNN and Fox News are all negligent in their willful abandonment of America, and American News. It’s actually been this way for a long time, but this story illustrates just how quick and wilful news services are to abandon their jobs of reporting ALL news… and worse, arbitrarily elevating minor news stories by self-labeling them as “major”.
Political Coverage
Prior to the Israeli coverage, these news networks have long had tunnel vision over all things Washington D.C. Again, instead of covering important news around the United States, these 4 networks have willfully abandoned this coverage in lieu of Donald Trump, MAGA and Joe Biden. Almost every word that has come out out of any of these network’s news anchors mouths in the last 12 months has been to do with one of those 3 topics: Trump, MAGA or Biden… until Hamas diverted them and Ukraine for a short time before that.
American news coverage doesn’t revolve around Washington D.C or politics or Israel or Ukraine. When the Israeli situation hit, all of these networks full-bore moved their political reporting firehose to the Israeli conflict and away from politics. What that now means is that D.C. politics might see 10 minutes of coverage in a day compared to the remainder of the 1430 minutes devoted to Israel (less their excessive commercial breaks).
Turning the News Off
When I tune into a news channel and within the first 5 minutes see the word “Hamas”, I tune out and go do something else. How many times can a news network say the same thing or reiterate the same point? At this moment, these news networks are now repeating the same diatribe over and over and over and over summed up to the following… “Israel good, Hamas BAD.”
Once you, as a news producer, can condense 24 hours worth of news into 4 small words, you’ve got a major problem to resolve. How many ways and times can a news network say the same 4 words?
Human Interest
Here’s one sickening turn of events in news reporting. A turn of events where news networks are also now failing us hard. When news networks can no longer figure out a way to say those same four words, they decide to vomit up some tear-jerker family story about the death of a loved one. We get it, people died in the conflict. We also grieve for their loss.
Instead, news networks feel the need to consume a large swath of their 24 hour OVER coverage with incidental and mostly irrelevant human interest stories. Oh yes, let’s pick a family and focus on THEIR story. Let’s understand how the mother and father became a shield to block gunfire for their children. It’s a terrible story, we get it. It’s human interest. Unfortunately, it exploits these family situations for ratings BY that news network. What the news network is doing to and with this family is far, far worse than anything else these news networks do. It exploits these unfortunate situations and those people involved to further a news network’s ratings, not help out the family. Human interest stories involving death should NEVER be considered news and should never be part of the news cycle.
Human interest stories have a place, but only when strictly labeled as human interest. Human interest stories should never be inserted in replacement of news coverage, especially in times of conflict reporting.
24 Hours In A Day
There are approximately 17 hours available for a news reporting day (subtracting the approximate 7 hours of commercials). Each of these news networks break their reporting up into blocks of hours using specific news hosts. You’d think that at least ONE of these hour blocks could give us a break from the Hamas cycle and report on (f)actual news around the nation. Instead, you’d be wrong. Every single block with every single news host CHOOSES to report on Israel and Hamas or Washington DC or Ukraine. Insanity!
When these channels go into tunnel vision mode, every single news program and news host rehashes the same exact information that the previous news host has already stated. It’s a vicious cycle that never ends. Until a news manager or producer decides to finally kill this news cycle entirely, we must suffer through this insufferable, constant barrage of the repetitive information, hour after hour after hour, day after day after day, maybe even week after week.
As a viewer, you could tune in and within 5 minutes get all of the information you need about that situation. You’d also be good for the remainder of that 24 hour period.
What this news over-coverage problem ultimately causes is viewers tuning out because of this repetition problem. It further means that real breaking news gets lost because fewer and fewer people are tuning in regularly. It also means that news viewers must turn to radio news or other alternative sources of news to avoid watching this homogeneous liquefied and over blended news coverage.
Will news channels ever get back to sensible coverage?
I can’t predict this. At some point, the pendulum may swing back. When it comes to commercial news networks like these, it’s sink or swim. The ratings will need to drop so low that the news producers have no choice but to begin making drastic programming decisions; decisions that will need to run counter to the news programming cycle being regurgitated on the other news networks.
Just because another news network chooses to do something stupid, that doesn’t mean every news network needs to do the exact same stupid thing and/or run the same exact amount of coverage. In fact, it’s better if not all news networks are doing the same thing. Let some of the channels deep dive into specific coverage, let others remain on a normal news cycle, reporting on ALL stories around the nation, interspersed with international news occasionally.
Fair and balanced reporting means reporting on all stories of interest, not latching onto one single story and tying it to your network 100% of the time. It seems incredibly stupid for every single news network to jump into tunnel vision reporting on one single topic. Yet, here we are.
News producers need to rethink this tunnel vision strategy going forward and grow a backbone. Producers need to stop torpedoing their own news channel’s ratings (and jeopardizing their own career) over this insane tunnel-vision single-news-topic round-the-clock stupidity.
PLEASE, finally get this memo.
↩︎
Safety: NVIDIA Shield Tablet Recall

If you have purchased an NVIDIA Shield Tablet in 2014 or 2015, it may be subject to a battery fire recall. This safety notice is very short. Let’s explore.
Which Tablets Are Vulnerable?
NVIDIA is recalling Shield tablets produced in 2014 and 2015 containing a Y01 battery type and that falls within certain models and serial numbers. To determine which battery type is in your NVIDIA Shield tablet, navigate to the following location on your in tablet’s Settings:
Settings => About tablet => Status => Battery
Under ‘Battery’, this area will display the type of battery installed. If the battery shown is type Y01, you should submit for a replacement tablet under this recall. If your tablet’s battery shows B01, then your tablet is not part of this recall.
My tablet is vulnerable! How do I submit for a replacement under this recall?
Good question.
Here is the link to NIVIDA’s web page regarding this recall. If you don’t trust clicking random links in pages, I don’t blame you. If would prefer to copy and paste the URL directly into your browser’s address bar, here’s the unclickable NVIDIA Shield Recall URL:
https://www.nvidia.com/en-us/shield/support/tabletrecall/
To submit your request for replacement, you’ll need to supply the following data to NVIDIA’s replacement form on the above NVIDIA page:
- Tablet Serial Number
- First Name
- Last Name
- Email Address
- Phone Number
- City
- State
- Zip
- Country
- Address 1 and/or Address 2
Then you must agree to the following:
I understand when I turn on my replacement tablet, my original tablet will be deactivated remotely and rendered unusable.
Once you have received the replacement tablet and you turn it on, your old tablet will be permanently remotely disabled. If you have personal data that you wish to keep on your affected tablet, such as photos, you should backup your tablet’s data before attempting to power on the replacement. It is also recommended to reset the affected tablet to factory default settings (which wipes all data from the tablet) before powering on the replacement tablet.
Good luck!
↩︎
A gag order won’t work on Trump

Trump is quite the chatterbox! This guy has about as much respect for the law and the judicial system as a cat has for water. Trump genuinely thinks he’s the star of his own show, that rules simply don’t apply to him.
Judges might as well be invisible, because their orders go in one ear and out the other! If you’re thinking a gag order will shut him up, you might as well try silencing a parrot with a whisper. Let’s dive into the delusional world of Trump and his disregard for legal boundaries. Grab your popcorn, folks, let’s explore!
What is a gag order?
A gag order is an order, typically a legal order by a court or government, restricting information or comment from being made public or passed onto any unauthorized third party.
In other words, a gag order is a legally binding order against an individual by a judge that if breached will cause the judge to apply penalties against the person who breached the order. The penalites could include fine and/or jail time. If the gagged person is indicted and out on bond pending trial, that bond could be rescinded and the person could be remanded into custody, then placed into jail and detained until the trial.
Donald Trump’s Mouth
The difficulty is that Donald Trump cannot shut up. He’s a voluminous talker and will not allow anyone to prevent him from speaking, least of all people who work for the agencies he believes to be corrupt.
What exactly does that mean for a gag order from the Department of Justice? It doesn’t mean a gag order will work. It does mean that that the government will have to end up making some hard choices. The only thing that issuing a gag order will do is cause Trump to breach it, thus the reason for those hard decisions.
From Trump’s so-called “raid” on Mar-A-Lago (which wasn’t a raid at all), we already know Trump doesn’t respect such legal matters and simply won’t abide. The question is not whether Trump can respect a gag order, it’s whether Jack Smith and the Justice Department are willing to rescind Trump’s bond after Trump breaches the gag order to then place him into protective custody until the Justice Department’s trial. Yeah… unlikely.
Why rescinding Trump’s bond is important!
The only way Trump can truly be gagged is to place him into protective custody until the DOJ (or any other) trial commences. Additionally, while in protective custody, Trump must be forced to surrender all of his electronic devices and have no contact with anyone until the trial begins. Unless (or until) this step is taken, Trump will not stop attempting to interfere with the trial including tampering with evidence, destroying evidence, tainting or coercing witnesses, threatening judges and threatening or tainting the jury pool.
Trump’s being under 4 indictments for many different alleged criminal activities has not cooled Trump at all in performing even more criminal activities. The average person placed under criminal indictment would stop doing whatever it was that got them there. Not Donald Trump.
Why is he continuing? Because Trump absolutely 100% wants to ensure that he will not receive a fair trial. Trump is doing everything in his power to ensure that his trial is entirely problematic and unfair from the start. That means that during trial or even after it, he will have sufficient evidence to prove that the trial wasn’t handled in a fair and equitable manner claiming that the jury judgement must be thrown out. It doesn’t mean that a judge will agree with Trump, but he’ll keep appealing all jury decision (assuming guilty) all the way to the Supreme court (where Trump has a lot of “friends” who will likely rule in his favor).
Presidential Election
As we should already know, Trump is again running for President in 2024. The difficulty is that Trump seems intent on using his campaign as a crutch to keep himself out of prison… or more specifically out of detainment before trial. That doesn’t mean he doesn’t want to be President again. He does. But… that won’t stop him from using his campaign as a means of preventing his detainment in jail pending trial.
As it is now, Trump is out on bond for all of his pending trials. Bond agreements stipulate that any further violation of laws or of court orders may result in rescinding that bond which means remanding the person into custody.
Trump’s Legal Woes
Just to be crystal clear, Trump is now facing 4 criminal trials, two of them federal. Let’s enumerate each of them now:
- Jack Smith’s Federal trial involving Classified Documents. This indictment contains 37 felony counts.
- Jack Smith’s Federal trial involving the January 6th Insurrection. This indictment contains 4 felony counts.
- Fani Willis’s trial involving Georgia State Election Interference. This RICO indictment contains 13 felony counts against Donald Trump, but also includes more counts against 18 other co-conspirators.
- Alvin Bragg’s trial involving Falsifying Business Records in New York State. This indictment contains 34 felony counts.
For more information on each of these trials, Politico has a good article on this.
Daring the Courts to Take Action
Trump is intentionally taunting the justice department, every judge and every prosecutor presiding over his court trials by inciting his cabal into action. By taunting, I mean calling out his cabal of goons to dox and death threaten these officials performing their jobs. There is also no sign of him stopping this behavior.
In fact, if Trump is given a true gag order, there is zero doubt he will breach that gag order, not once, but many, many, many times. It’s not a matter of if, it’s a matter of when… but that’s not what matters.
What matters is how each trial judge will handle the breaches and what decision they will make involving those breaches. There are 4 pending trials, but only one trial judge can put him behind bars until their trial. If that judge is the one presiding over the federal trial, how will the 3 other trials proceed if he’s stuck in federal detainment?
It’s worse than simply just detaining him. Trump is absolutely begging the judges to attempt to gag him because he knows they won’t detain him in jail pending trial. They know that these judges do not have the spine to place a Presidential candidate behind bars pending trial. If the gag orders don’t work, and they most certainly will not, then what besides protective custody? Fining Trump again is fruitless. Not only will he not pay that bill, he won’t stop talking.
Gag orders won’t work because they simply can’t work on Donald Trump. With anyone else, a breached gag order for someone indicted would instantly lead to detainment in jail pending trial. With Trump, that’s not easily possible.
Again, it’s not what Trump does after he breaches a gag order, it’s what will each of the trial judges and the indicting prosecutors do when he does… and he most definitely will.
Will they attempt to detain him? Likely not.
Will a fine work? Definitely not.
Will Trump stop talking? No.
Where do we go from here?
Clearly, the prosecuting attorneys and the judges will have some intense soul searching to do. How do you reign in a person in this situation? Either they’ll need to devise a creative new solution or they’ll have to let Donald Trump slide.
I’d love to see these judges remand Trump into custody pending trial. However, I just don’t see that happening. No judge is likely willing to put their own career on the line to jail a former President… especially when he’s the purported front runner of the GOP. I personally don’t think that makes any difference. If a person has committed an alleged crime, then they need to be treated as any other person, regardless of their present role or aspirations.
The only clear choice for penalities is to move the trial up after each breach. Just as Judge Chutkin warned Trump, so too must Jack Smith and every other trial judge. For each breach Trump makes against a gag order, the trial gets moved earlier by one month. It’s the only solution to this dilemma. If they can’t or won’t jail him and take away his voice, then they must penalize him in other ways that hurt his chances at trial.
Trump should be sitting in pretrial detainment today. He shouldn’t even have been given a bond. On the campaign trail? Too bad, so sad, not my (or anyone else’s) problem other than Trump. If Trump wanted to be on the campaign trail, he should have ensured he didn’t break any laws prior to getting there. Pretrial detainment is the only answer to get Trump to comply with a gag order. Unfortunately, it will likely never happen.
Overall, these judges must make some hard choices if they wish to retain civility in their courts. Trump is intent on turning every trial into an unfair circus. It is the judges who must determine the best way to reign in Trump, but it is also crystal clear that Trump will not abide by any traditional legal approaches.
↩︎
Fact Check: Time article claims Phenylephrine ineffective.
 Welcome to the new Randocity Fact Check Series. With all of today’s lies, deception with intentional and wilful misleading information, Randocity is beginning this series to combat these misleading and false articles. With that said, a recent Time article blanketly claims Phenylephrine is ineffective. Let’s explore.
Welcome to the new Randocity Fact Check Series. With all of today’s lies, deception with intentional and wilful misleading information, Randocity is beginning this series to combat these misleading and false articles. With that said, a recent Time article blanketly claims Phenylephrine is ineffective. Let’s explore.
Time Article
The Time article in question is entitled “With the Decongestant SNAFU, the FDA Tries Something New” written by Haley Weiss and published on September 14, 2023 4:30 PM EDT. Note, the link included points to the article’s contents located at the Wayback Machine at the Internet Archive to show this article’s snapshot as it was written at the time this article was published. I offer a link to the actual Time article later in this article, but I suspect this article will be corrected soon, thus the snapshot is required. Please click the Wayback Machine link to read this article in full.
Because Time and other large media outlets have tendencies to revise, correct and sometimes delete articles at later dates, the Wayback Machine is the only safe way to maintain a consistent link to such articles from the past. Let’s move on.
Misleading Information
The trouble even with sites like Time is that they hire writers who don’t always properly investigate or clarify the information about which they are writing. In this case, Haley Weiss doesn’t properly clarify her article’s own topic.
Here is Ms. Weiss’s relevant misleading statement in her article:
…the panel of experts assigned to evaluate over-the-counter allergy medications ruled that phenylephrine was effective.
Except phenylephrine has never worked. What’s puzzling, then, is how it stayed on those shelves for 50 years without a challenge.
Note: Highlighting and text formatting added by Randocity for fact checking and clarification purposes.
This unusual blanket statement regarding Phenylephrine is entirely misleading. The article opens by not outright stating the fact that the entire article’s premise involves discussion solely around oral administered versions of Phenylephrine. Simultaneously, this article makes no mention of nasal spray versions of this drug. It is, thus, left up to the reader to understand and discern (and not conflate) this fine point. Conflation is the problem at issue here.
The reality is, either Haley is intentionally trying to mislead readers into believing that all forms of Phenylephrine don’t work or Haley is naive and doesn’t understand (or didn’t research) that multiple administration forms of Phenylephrine exist. Being a health columnist for Time, I find the latter to be extremely unlikely and improbable.
In this article, Haley seems to be intentionally trying to conflate all forms of Phenylephrine under the same “doesn’t work” umbrella, when clearly this is not true.
Nasal Spray Administration
While oral pills and oral suspensions appear to be the sole focus of Haley’s Time article, this article also conveniently ignores the fact that the drug Phenylephrine is also available in a Nasal Spray format. In fact, several known brands utilize this drug ingredient including the brand Neo-Synephrine… and, yes, this brand has been on store shelves for years. The form of Phenylephrine used in a nasal spray is Phenylephrine HCL.
When Phenylephrine HCL is administered using a nasal spray, this drug is, contrary to Haley’s misleading assertion in her Time article, quite effective and fast acting at opening up nasal passages when applied directly to nasal mucosa tissues, thus shrinking (or constricting) them. This author has used Neo-Synephrine for years for this purpose. I can also attest personally that Phenylephrine HCL is not only QUITE effective, it’s also fast acting and usually starts working within 1-3 minutes.
The downside to Neo-Synephrine (Phenylephrine HCL) is that it is short acting and requires frequent re-application. The best duration I’ve been able to get out of this nasal spray is between 1 and 3 hours of relief.
How I use this specific nasal spray is for the near instant relief it offers (1-3 minutes), opening up nasal passages rapidly. I then couple Neo-Synephrine with a second spray from the longer acting Afrin. Afrin contains Oxymetazoline HCL, which this drug lasts between 6-12 hours in duration, depending on amount of nasal discharge. The more discharge, the faster it wears off. However, Afrin’s active ingredient (Oxymetazoline HCL) takes up to 15 minutes to begin working after being sprayed… which is why I couple up Afrin with Neo-Synephrine. Waiting 15 minutes for a nasal spray to begin working takes way too long.
Neo-Synephrine gives me short and immediately relief. Afrin gives me long continuous relief long after the Neo-Synephrine has worn off.
Compare all of this to saline spray. While saline sprays are effective at washing nasal tissues, it does nothing to actively open up the nasal passages. If the saline manages to dislodge and wash away an allergen irritant, it might help reduce nasal allergies. However, I’ve never had any congestion relief from using a saline nasal spray, other than to sooth irritation and dryness.
Nasal Sprays are Drying
The one thing that drugs like Oxymetazoline HCL and Phenylephrine HCL have in common is that they are extremely drying to nasal muscosa. They are so drying, in fact, that they can sometimes cause nose bleeds. The best way to avoid this drying problem is to occasionally apply a saline spray to keep the nasal tissues hydrated while using Phenylephrine HCL and/or Oxymetazoline HCL. You can also use a facial steamer to steam the nasal passages, help hydrate them and offer relief from the dryness.
Nasal Spray Rebound
All of the current drugs that are designed to shrink nasal mucosa (vasoconstriction) by direct spray application have the possibility of a rebound effect. Nasal spray rebound is when the drug wears off and the nasal passages stay congested for long periods thereafter… sometimes for hours. This then causes the person with congestion discomfort to want to spray again to open up the nasal passages. It becomes a vicious cycle.
I workaround rebound by cessation of spraying one side at a time. I cease using the nasal spray in one nostril and wait through the rebound cycle to complete for that one side, which could take up to 24 hours. Once the rebound is over and that nostril is back to its normal state, I then cease using nasal spray in the other nostril and, again, wait through the rebound cycle. Once both nostrils are clear, I’m off of the nasal spray.
This is the only method I have found to get out from under the nasal spray rebound cycle. I go through this process with each cold I’ve had at the very end of the cold. There’s no real way to avoid nasal spray rebound, unfortunately.
Rebound is the reason that so many people get addicted to using nasal spray.
Nasal Spray Effectiveness
The final aspect of the use of any vasoconstricting nasal sprays is that they’re actually too effective. What I mean by “too effective” is that these sprays artificially open the nasal passages wider than is otherwise normal. It forces the nasal muscosa to shrink more than is normal when the nasal passages are open under normal circumstances. For me, this being “open too wide” causes several problems.
The first problem of being too open is that it allows way more allergens in, which causes me to sneeze way more often. The second problem is that I can feel that the passages are open too wide, which actually causes a slight bit of discomfort. Third, because the passages are open quite wide, this encourages way more air flow in and out, which seems to cause more drying than is otherwise normal. Thus, the need for saline sprays or steam treatments to moisturize. While the drug formulations also seem to encourage dryness via the drug chemical itself, the being open too wide seems to exacerbate this drying issue.
However, if the choice is being fully congested or using a spray to open nasal passages, I’ll choose using the spray every time. My first spray choice is always Neo-Synephrine because of its fast acting nature, even though it doesn’t last nearly as long as Afrin.
Time Article, Circling Back
The point to all of the above is that Phenylephrine is indeed effective and useful when applied in the correct way. However, when taken in an oral form, its effectiveness may be in question as Haley’s Time article suggests.
I don’t have a problem with Haley’s article if seen solely through the lens the oral drug versions. However, her article is confused and appears to intentionally conflate all versions of Phenylephrine to be one-in-the-same. They aren’t. While the oral versions may be ineffective and have no efficacy, the same absolutely cannot be said of the nasal spray version.
Debunking Haley Weiss Time Article
Haley Weiss’s article in Time (this is the actual Time article link) is strongly misleading. It intentionally attempts to lump all forms of Phenylephrine into the same bucket, claiming the overall drug is ineffective and does not work.
===> This article’s claim is absolutely false! <====
Phenylephrine HCL in a nasal spray format is quite effective as a decongestant when applied directly in the nasal passages. Phenylephrine, when taken in an oral pill or suspension format, as her article suggests, may or may not be effective for the purposes for which it was intended, as an oral decongestant. This article intentionally fails to separate the effective uses of this drug from its ineffective uses, thus making overall blanket statements to confuse readers.
I guess that Time is no longer a trustworthy enough news source to properly research its articles… nor can it now avoid making such misleading statements.
↩︎
New Music Monday: Makeba by Jain
While the Makeba song is already several years old (released in 2015 on Jain’s debut album, Zanaka), it is receiving a lot of recent air play thanks to TikTok. Here’s a session of Jain performing Makeba live using a very creative sampling device. Watch her create the samples from her instant live vocals and then reuse them to create this song.
Jain (Jeanne Louise Galice) is a French singer who came to prominence in 2015 via her debut album, Zanaka. Since then, she has released two additional full length studio albums, Souldier (2018) and The Fool (2023). Let’s take a dive back in time to relive the dance favorite Makeba, but also make it new again.
Fantastic!
↩︎
The design failure of SE Linux?

Buckle up, folks. Let’s embark on a wild and whimsical journey into the quirky world of SE Linux. Oh yes, we’re diving deep into the mysterious realm of this oh-so-important “security” thingamajig, which may sound a bit dull, but trust us, it’s secretly fascinating. Grab your virtual popcorn and Starbucks, sit back, and let’s unravel this enigmatic Linux subsystem together! Let’s explore.
What is SE Linux?
SE Linux stands for Security Enhanced Linux (SEL); a catch phrase more or less. Developers love giving their add-ons names like SE Linux. In reality, what does SE Linux actually do? The name doesn’t really say. It does say it has something to do with security, but short of digging deep into documentation, you really have no idea what SE Linux really is.
Let me start by saying that SE Linux makes Linux incompatible with standard written applications. Why? Security Enhanced Linux attempts to lock down the internals of Linux, but it does so in a way that breaks nearly every single regular application ever written. In essence, enabling SE Linux is sure to break all of your third party apps.
Why does SE Linux break the apps? Because SE Linux is given complete control to restrict access of components down to the function() call level and down to a content serving level. What that means is that a function call like execve() could receive “access denied” if a program were to attempt to use it with SE Linux enabled… yes, even if the program is operating as “root” user. Even serving up HTTP content over a path that shouldn’t have HTTP content could be denied.
Because the “root” user has always had unbridled access to EVERYTHING in an operating system, allowing SE Linux to constrain the “root” user’s access to no more than a regular user automatically breaks the idea of what Linux is.
SE Linux Modes
Before getting too deep into the weeds, someone is likely to point out that there are two modes to SE Linux when operating: 1) Permissive and 2) Enforcing. Unfortunately, the “Permissive” mode isn’t as permissive as one would hope and it’s a more-or-less useless operating mode intended strictly for testing purposes. Even enabling “Permissive” can still break applications simply because “Permissive” isn’t exactly the same has having SE Linux disabled entirely.
 When SE Linux is entirely disabled, this is (and was) the natural state of Linux (and UNIX) since the day UNIX was first introduced. The problem is, SE Linux was designed by the NSA (National Security Agency) as patches to Linux and, more specifically, to Linux’s kernel. The NSA isn’t really a software developer. As such, this agency has shoe-horned into Linux a system that not only fundamentally breaks UNIX, it fundamentally changes Linux and UNIX into something other than UNIX.
When SE Linux is entirely disabled, this is (and was) the natural state of Linux (and UNIX) since the day UNIX was first introduced. The problem is, SE Linux was designed by the NSA (National Security Agency) as patches to Linux and, more specifically, to Linux’s kernel. The NSA isn’t really a software developer. As such, this agency has shoe-horned into Linux a system that not only fundamentally breaks UNIX, it fundamentally changes Linux and UNIX into something other than UNIX.
UNIX was founded on the principal that it should work in a very specific way, a way that enhances computing. Unfortunately, SE Linux has shoehorned its way into the operating system as a watchdog system that’s sole purpose is to get in the way of computing; to be that crossing guard who throws up a STOP sign and prevents you from crossing… even if you’re a firetruck on the way to a fire.
Linux Security
Linux has always been a relatively secure operating system, so long as you maintain good password quality, close down unnecessary and unneeded services, regularly maintain security patches and utilize best practices when installing new software. Combining all of these proactive management best practices with a solid firewall, it’s relatively unheard of for a Linux system to be broken into, let alone exploited with malicious code. Nearly all deployed malicious code found on Linux servers is due to hackers having gained root access to the server and then manually having installed it.
Yet, the NSA felt that it was necessary to effectively break Linux to introduce a “new” watchdog system that watches every system call being used on the operating system. More than just watching it, it must interfere with some of these calls, preventing them from occurring.
This doesn’t just break Linux, it guts Linux into oblivion. It’s no wonder then why the vast majority of sites (and managers) running Linux, disable SE Linux as first thing before deploying a new server. Who wants to have to deal with broken software?
Third Party Software
You would think third party software manufacturers would have embraced SE Linux due to its alleged extra security. Instead, you’d have thought wrong. Most manufacturers still don’t embrace SE Linux due to its hodge-podge nature. It doesn’t help that most systems administrators and systems managers also don’t understand SE Linux or its internals… but that’s not the real problem.
The real problem is the developers. Developers build their software on laptops and other convenient computers running Linux, but they disable SE Linux so that it doesn’t get in their way when writing code. Writing and testing code is difficult enough without having to debug SE Linux when code failures begin. By disabling SE Linux, developers take that annoyance out of the equation. Rightly so. Why have a subsystem enabled that’s sole purpose is to get in your way?
The problem is, without developing code WITH SE Linux running, that throws the problem onto the systems administrators and/or systems engineers to solve after-the-fact. The developer is all, “Here you go” (handing the system engineer the finished software), leaving the systems engineer the problem of attempting to get the software working with SE Linux enabled. Most times, that ask is impossible. A systems engineer doesn’t have access to the source code. So, they can’t guide the developer to rewrite or redo portions of the code to make it compatible with SE Linux.
What that ultimately means is that SE Linux gets disabled on production servers simply to deploy that developer’s code. Without every developer both enabling and understanding SE Linux on their development servers and, most importantly, using it during software development, there is no way a systems administrator or systems engineer can make it work with SE Linux after-the-fact. Software is either designed to work properly within the constraints of SE Linux or it is not.
This is the fundamental problem with the compatibility level of SE Linux. This is also a primary design failure of SE Linux by the NSA, that and SEL’s failure to actually secure the server. In other words, new subsystems must remain fully backward compatible to what has come before. If it can’t remain backwards compatible, then it ultimately won’t be used… and that’s actually where we are.
DOD and SE Linux
To be certified by the Department of Defense (DOD) per Security Technical Implementation Guide (STIG) compliance, a UNIX system must enable SE Linux as ‘Enforcing’ (the strongest level offered). For those companies who wish to do business with the government, or more specifically with the Department of Defense, STIG compliance is a must. By extension, STIG compliance does mean enabling SE Linux (in among a whole slew of additional DOD security requirements).
Businesses must then make a choice. Seek to do business with the US Government or not. If you’re running Linux operating systems as part of whatever service you intend to offer to the US Government, you must comply with the requirements defined in the Defense Information Systems Agency’s (DISA’s) STIGs (which, as stated above, includes enabling SE Linux… and all that falls out of that).
Are there ways around SE Linux’s Incompatibility?
Yes, but it’s not always easy or fast. Heads up. This is the dull part. So as not to dive too deep into the sysadmin weeds as to why, here’s a comprehensive RedHat guide of SE Linux’s incompatibility (and how to get around it all). However, we will still need to dive deep enough to get this article’s point across.
For example, customizing an HTTP configuration as so (a normal thing to do for Apache HTTP), yet this customization would yield the following problems when SE Linux is enabled:
The http package is installed and the Apache HTTP server is configured to listen on TCP port 3131 and to use the /var/test_www/ directory instead of the default /var/www directory or the default port of 80. # systemctl start httpd # systemctl status httpd ... httpd[14523]: (13)Permission denied: AH00072: make_sock: could not bind to address [::]:3131 ... systemd[1]: Failed to start The Apache HTTP Server.
With SE Linux disabled on a Linux system, Apache’s HTTP server would happily start up just fine. With SE Linux enabled and set to ‘Enforcing‘, starting httpd with the above modified config, you’ll see “Permission Denied” at the point when httpd attempts to bind to port 3131.
It gets worse. To modify SE Linux to allow httpd to listen on port 3131, you have to execute the following SE Linux permission modification command:
semanage port -a -t http_port_t -p tcp 3131
That’s just the beginning. Even after executing this semanage command… then restarting HTTP, the change in directory yields the following error when attempting to retrieve content:
# wget localhost:3131/index.html
...
HTTP request sent, awaiting response... 403 Forbidden
Why 403 Forbidden? Well duh…
# sealert -l "*"
...
SELinux is preventing httpd from getattr access on the
file /var/test_www/html/index.html.
...
SE Linux has prevented access to the getattr() function for /var/test_www/html/index.html. This again requires manually reconfiguring SE Linux to allow this new directory location for httpd. Though, we must understand why SE Linux doesn’t like this path and file.
# matchpathcon /var/www/html /var/test_www/html
/var/www/html system_u:object_r:httpd_sys_content_t:s0
/var/test_www/html system_u:object_r:var_t:s0
The SE Linux command matchpathcon (so intuitively named here) determines that the content type used in /var/www/html (the standard default location) isn’t the same as what’s defined for /var/test_www/html. Thus, SE Linux won’t allow HTML content to be served from that customized directory when HTML content is not defined. Can we say, “minutiae?” I knew that you could.
That means redefining the content type for /var/test_www/html to allow serving httpd_sys_content_t type. To do that, a system admin would need to execute the following:
# semanage fcontext -a -e /var/www /var/test_www
BUT, that command executed just above doesn’t actually do it recursively for all files and dirs within /var/test_www. Oh, no no no. Now you have to run yet another command to force recursion to set all sub-directories and files to allow for httpd_sys_content_t type of data. You do that with…
# restorecon -Rv /var/
...
Relabeled /var/test_www/html from unconfined_u:object_r:var_t:s0 to
unconfined_u:object_r:httpd_sys_content_t:s0
Relabeled /var/test_www/html/index.html from unconfined_u:object_r:var_t:s0 to
unconfined_u:object_r:httpd_sys_content_t:s0
A systems administrator can spend all of the above time to do all of this additional reconfiguration work each and every time a new web directory is needed…. OR, a systems administrator can disable SE Linux and avoid all of this work.
Janitorial Work
Even if you don’t understand a word of what was said just above, it’s easy to see that it’s an absolute mess. Not only does SE Linux require a systems administrator to configure all of this extra junk, it requires a systems administrator to understand all of the above NEW commands needed to manage SE Linux AND have a firm grasp of all of these commands’ nuances and quirks. Even missing one tiny thing can cause the whole application to break or fail to work in unexplained ways.
For example, the 403 Forbidden error could have led an inexperienced systems admin down a rabbit hole simply because they don’t know that SE Linux is enabled as ‘Enforcing’. Such inexperience might not allow putting two-and-two together to understand that SE Linux is actually the culprit.
It’s easy to see why many, many businesses running Linux make it a policy to instantly disable SE Linux. If your company is not doing business with the government, there’s no need to make your systems administrators do all of this extra work when they could be performing other more critical tasks.
On the flip side, if your business is currently negotiating with the DOD for a contract, then you better get your systems administrators trained up quick on SE Linux. More than this, you better run an audit to determine which software your business uses to determine if this software is easily made compatible with SE Linux. Hint: it probably isn’t easy.
DOD Exceptions?
Does the DOD allow for exceptions? Yes, but limited and likely only for a limited time. Meaning, if you can’t enable SE Linux right away due to software limitations, you’ll need to document exactly why. Even then, your team better have a plan to get SE Linux implemented soon or else your contract might dry up. It only takes another vendor to step up that IS fully compliant with DISA STIGS for your company to lose its contract.
Does SE Linux improve security?
This is actually a very good question. The short answer is, no. SE Linux requires a system administrator to drastically increase workload to manage application permissions. However, SE Linux also forces an administrator to explicitly define permissions for each application down to incredible minutia. Once that long-tailed convoluted configuration is complete, the application then works again like it always has (i.e., without SE Linux).
Here’s the key! Because most exploits rely on standard app functionality to work, SE Linux would happily allow an exploit to occur simply via performing that application’s normal functions. The only exception would be is if the systems administrator explicitly disallowed use of specific system function calls. However, if an application uses that function call even once during normal operation, having the system administrator disallow that call could cause the application to fail in very unexpected ways, possibly even leading to an OS cascade failure / core dump.
Further, SE Linux is effectively an enhanced permissions system, but it does nothing to watchdog an application’s behaviors to ensure that the application itself is functioning correctly or normally.
What this further means is that a system administrator would need to become a software developer to read through and understand the entire application’s source code to know when or if an application uses a specific function call that the administrator wishes to deny. While many systems administrators can be programmers, not all of them are. More than this, many systems administrators who can code are barely more than novices. Were a systems administrator actually a software developer in disguise, then why would they remain a systems administrator by trade? Thus, most systems administrators know enough to read some code (i.e., novice), but not enough to actually write complex code.
Let’s take this one step further. Putting a system administrator in the position of unilaterally denying access to specific function calls is not what systems administrators are tasked to do. That’s defining policy. That’s not an SA’s job. Expecting an SA to take on this type of job turns an SA into a security manager or policy manager, not a systems administrator. Systems administration is exactly how those two words sound: administration of systems. Meaning, management of systems, making sure those systems operate fine, occasionally install software and/or operating systems, manage configurations of systems and debug it all when it doesn’t work correctly. Systems administrators are even tasked with winding down old hardware and systems to dispose of them.
Systems administrators don’t make policy, but will enforce policy as defined by managers… so long as that policy makes sense and doesn’t interfere with the operation of the network, server or application. However, not all systems administrators are knowledgeable enough to foresee if any specific policy change might end in bad results.
Policy Implementation
Here’s a situation that can get systems administrators into hot water easily. Managers all congregate and decide to implement a new policy that execve() cannot be called from within any application. The policy is handed to a systems administrator to implement. The SA is relatively new and doesn’t understand either the systems fully or the software operating on those systems. The SA does understand SE Linux enough to implement the change as requested and, thus, does so.
Within an hour (or less), the company’s primary paid application is down, the servers are behaving erratically, memory is spiking and the systems are actually crashing and rebooting. Effectively, the business’s servers are down.
Here’s a situation where the company’s executives made an unwise and untested decision and forced implementation down onto a person with very little experience. The person happily obliged thinking the managers already knew it would work. Why would these managers expect a new SA to jump through many hoops testing all of this? The SA would assume that if the request landed on his/her desk, it must already be tested.
Yet, it wasn’t. Here’s the rub. Because the SA did the actual work to implement the change to the systems, the SA will be held responsible for the outage (possibly up to and including termination). Ideas from managers never get blamed. The people who get blamed are the systems administrators who “should have known better” and, specifically, the person who actually “pulled the trigger” by performing the configuration change.
Enabling SE Linux as ‘Enforcing’ is the same situation. If you ask your SA team to implement this change without performing any testing, then expect your business to go down. Almost no applications are properly configured to handle SE Linux set to ‘Enforcing’ prior to enabling it.
Heading down the SE Linux Road
If a company wishes to implement SE Linux as ‘Enforcing’, then you best test, test, test and then test some more. You can’t just turn SEL on like a light and expect it all to work just as it had. Making this decision means testing. More than this, it means ensuring all systems administrators are not only familiar with SE Linux itself (and its commands), but also are familiar with all applications installed and running on the company’s servers.
Once SEL is enabled, the applications are likely to begin failing unless the systems administrators have already configured those specific applications under SEL before.
What have we learned?
Let’s explore all that we’ve learned about SE Linux.
- SE Linux is a deep dive permissions system add-on for Linux. It primarily enhances security through obscurity. We already know that security through obscurity doesn’t work.
- SE Linux is fraught with peril. Unless systems administrators are properly trained to both understand SEL and how to configure apps under SEL, enabling SEL can lead to problems.
- SE Linux doesn’t improve security because once apps are configured under SEL, they are just as vulnerable to being exploited as if SEL were not enabled.
- SE Linux increases workload for systems administrators because not only do they need to do their normal Linux administration jobs, they must also deep dive into SE Linux a lot to make sure it is and remains correctly configured and functional.
- SE Linux is an overall hassle to manage.
- SE Linux is not required unless you’re attempting to win a contract with the United States Department of Defense.
Overall, the design behind SE Linux seemed to have noble intentions. Unfortunately, SE Linux is actually much the same as requiring someone to spend time hanging padlocks off of a chain-link fence as illustrated in this article’s opening. Unfortunately, those padlocks don’t serve to protect that fence. The fence is still doing all of the protection work.
However, these padlocks symbolize the exact way that SE Linux attempts to protect an operating system. The operating system is the chain link fence… and the OS does all of the protection. The padlocks (SEL) only serve to clutter up that fence, but don’t actually do much of anything to improve security.
↩︎
Analysis: Jack Smith’s 2020 Election Indictment
 Let me start this article out by saying that I am not a Republican, nor do I much like Donald Trump either as a politician or as a person. He’s a vile, pathological lying, bigoted and overall crass person. The man literally has almost no redeeming values. With that said, I also don’t like when even the vilest of persons, like Donald Trump, isn’t getting a fair shake. Let’s explore.
Let me start this article out by saying that I am not a Republican, nor do I much like Donald Trump either as a politician or as a person. He’s a vile, pathological lying, bigoted and overall crass person. The man literally has almost no redeeming values. With that said, I also don’t like when even the vilest of persons, like Donald Trump, isn’t getting a fair shake. Let’s explore.
Jack Smith’s 2020 Election Indictment
I recently published a news article discussing this very indictment. I’ve withheld making any comments over this indictment solely because that information was newsworthy. Meaning, passing along this information timely to Randocity’s readers was important. Yes, it is important. However, there are some problems with this indictment that few news channels are discussing. The first and biggest problem is…
Presidential Immunity
Many of the statements included in Jack Smith’s indictment were made while then President Trump was still a sitting President. He made the statements while officially holding the office of President of the United States.
The President of the United States is entitled to Absolute Presidential Immunity, shielding the President from lawsuits while performing business as President. However, some in the judicial system believe that Presidential Immunity is not absolute, meaning that criminal conduct performed by the President (outside of Presidential job responsibilities) may not be immune from prosecution.
I’m not convinced that that’s the correct course for the United States. While I don’t want rogue Presidents performing illegal criminal actions, I also don’t want the DOJ able to apply spurious lawsuits on either a sitting President or, more importantly, a former President after-the-fact.
The question remains, were the statements that President Trump made regarding January 6th and those involving the placement of fake electors considered within the job role of President? While I would love to say, “No”, I am not in a position to make that judgement. Only a court can. That means it’s the responsibility of Jack Smith to have a court determine if Trump’s statements are admissible towards the case he is bringing. Meaning, many of the statements made by Trump included in Jack Smith’s indictment were made while Donald Trump was still President.
The question is then whether the statements are protected by Presidential Immunity. Jack Smith would need to first establish if any or all of Trump’s statements can be admitted as evidence or if they must be excluded as part of Presidential Immunity that Trump held at the time.
“At the time”
Here’s another problem that is born out of the above. Presidential Immunity is clearly active while a person is actively holding office as President of the United States. Once a person leaves office and becomes a former President, all of the acts performed AS PRESIDENT should still remain protected under Presidential Immunity. If not, it means that as a former President, all actions made by a then President can, at the time they become an ex-President, become fodder for criminal litigation.
If America starts trying and convicting each and every President as soon as they leave office, where are we as nation? More than this, does Presidential Immunity really exist? No. Actions performed by a President during his or her tenure in office must remain sacrosanct even after leaving office. Those actions were performed while faithfully executing the duties as President. Even when the person leaves office and becomes an ex-President, those Presidential years remain a sacrosanct bubble protected by Presidential Immunity in perpetuity. That means that an ex-President cannot be tried for actions performed WHILE President after becoming an ex-President.
This should go without saying. If America allows the justice system to begin prosecuting every former President for actions performed while in office, who would ever want to become President?
However, any person who is not President CAN be tried and convicted for actions performed while NOT President, either before being elected or after becoming an ex-President.
Jack Smith is Barking up the Wrong Tree
There were many ways a lawsuit could manifest against Donald Trump involving January 6th, such as involving Treason and Sedition, neither of which are named in Jack’s current lawsuit as charges. Both Treason and Sedition are high enough and serious enough crimes that these charges would easily negate Presidential Immunity by a landslide. After all, no President should need to ever perform Sedition or Treason in the execution of Presidential duties and responsibilities.
On the other hand, the four counts levied by Jack Smith are as follows:
- 18 U.S.C. § 371 — Conspiracy to Defraud the United States
- 18 U.S.C. § 1512(k) — Conspiracy to Obstruct an Official Proceeding
- 18 U.S.C. §§ 1512(c)(2), 2 — Obstruction of and Attempt to Obstruct an Official Proceeding
- 18 U.S.C. § 241 — Conspiracy against Rights
These obstruction and plain-old conspiracy charges don’t instantly negate Presidential Immunity. In fact, these charges are a bit open for being contested. These above crimes are not necessarily serious enough to warrant dropping Presidential Immunity over them and can also be interpreted in ways that make the prosecutor appear prejudicial (i.e., biased) towards the defendant.
Thus, the indictment Jack Smith has brought is fraught with problems, specifically around statements and actions made and also the specific charges being levied, all while Donald Trump still actively held Presidential Immunity.
Unnamed co-conspirators hold no such immunity from prosecution. These people should be brought up on charges for the actions they performed and statements they made around the 2020 Election, including newscasters and congressional members. However, Donald Trump’s statements and actions shouldn’t be used to prosecute Donald Trump while Trump still held Presidential Immunity, at least not until Jack Smith has a court determine which statements (and actions) ARE and ARE NOT protected by that Immunity. Until the Presidential Immunity issue is resolved, Jack Smith is barking up the wrong prosecutorial tree.
In fact, Jack’s whole indictment now actually does look like a witch hunt as Donald Trump suggests. Without first resolving whether Trump’s statements were protect by Presidential Immunity, transcribing those statements into an indictment is extremely risky and premature AND makes Jack Smith look like he’s rushing to get this lawsuit done, but quite improperly and with prejudice.
A prosecutor can’t simply dismiss steps because they’re inconvenient or slow the process. Unfortunately, making missteps like this only serves to weaken Jack’s case against Donald Trump, probably giving Trump the opportunity to have the entire case dismissed based on prejudicial treatment.
Instead, I would have preferred if Jack Smith had had a court first determine whether the statements transcribed are or are not, in fact, protected by Presidential Immunity. Let’s resolve this issue first. If some or all statements are protected by Presidential Immunity, then the statements cannot be held as evidence against Donald Trump or against Donald Trump’s alleged actions for the charges being levied.
Better, revise the charges to include Sedition and Treason so that there is no question as to whether Presidential Immunity is involved.
↩︎






leave a comment